VoIP Monitor
Voice over IP (VoIP) systems are gaining in popularity as the technology for transmitting voice traffic over IP networks. While VoIP technology is set to revolutionize communications, and is already being used by a number of traditional telephone companies to connect their regional offices, on a smaller scale it can also be a useful solution for businesses looking to trim their telephone expenses.
As the popularity of VoIP systems increases, they are being subjected to different kinds of intrusions, some of which are specific to such systems, and some of which follow a general pattern of attacks against an IP infrastructure. Crystal Eye’s VoIP Monitor app generates reports which provide insights on a broad range of VoIP protocol based attacks patterns. Appropriate collection and observation of these app generated reports helps to trace the attack once it has happened.
The data generated by the VoIP Monitor app provides specific information related to potential attacks displayed as alerts in the VoIP Monitor section. The data can be analyzed to know the time and date of the attack, the source IP address of the attacker, the destination IP address of the affected machine, the country from where the attack originated, attack description, and the rule that generated the alert (attack type).
The VoIP Monitor application is installed by default and can be accessed from the left-hand navigation panel.
Left-hand Navigation Panel > Reports > VoIP Monitor App
The VoIP Monitor reports can be used to gain insights on various attacks generated through VoIP protocols. The attacks against such VoIP systems span a large class, from denial of service to billing fraud. These apps generated reports are analyzed to understand the nature of threats to be dealt with and the also gives the required clues to trace the attacks.
How to View the Details of a Potential Attack on a VoIP System?
Step 1: In the VoIP Monitor app page, select the time period for which the report is required from the Select Report dropdown.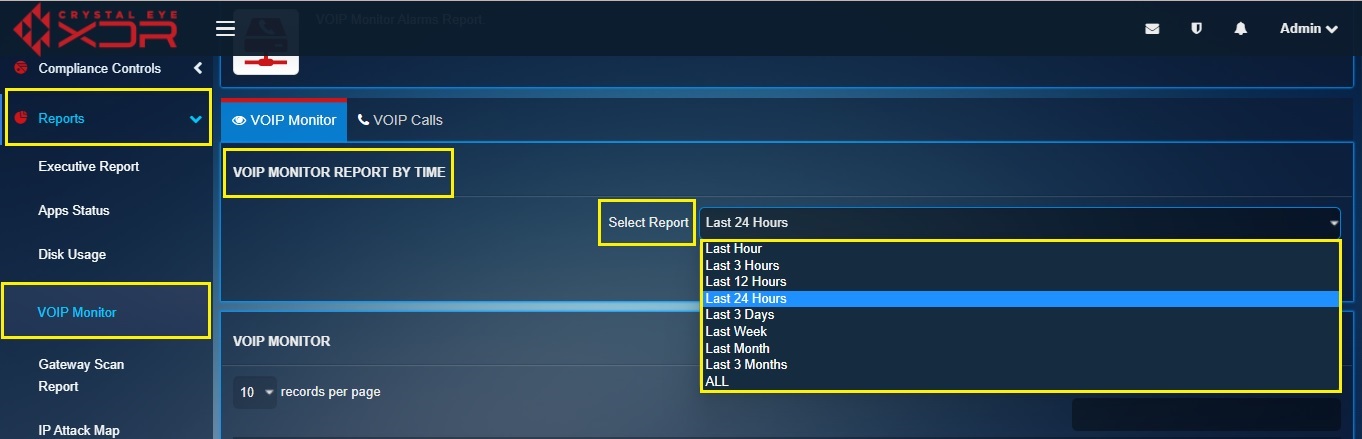
Step 2: You will now see data of a range of potential VoIP protocol related attacks in the VoIP Monitor section.
Note: You will be able to view the time and date of the attack in the Timestamp column, the Source IP address from where the attack originated, the Destination IP address of the affected system, the Country from where the attack originated, the Description of the attack, and the Rule Type that triggered the alert.