Incident and Event Services SIEM
Crystal Eye XDR's SIEM collates metadata from across an organisation’s technology stack to provide monitoring and incident identification. The integration of these inputs within the Crystal Eye Operating System therefore offers broad visibility across networked systems which in turn provides more sophisticated threat detection through a deeper analysis of events. This orchestration also includes live event feeds from end points through on-demand event discovery that further enhances visibility for incident responders.
The SIEM app helps to manage various settings that defines the levels of security analysis done by Red Piranha’s Security Operations Team. Crystal Eye offers three security service levels namely, Level – 1 Silver, Level 2 - Gold and Level 3 - Platinum. The system also prompts the user to feed in the primary and secondary contact details which is used to contact the users by Red Piranha Security Operations Team for various security related correspondences. The administrator can also start and stop the SIEM Agent installed in the Crystal Eye appliance.
The Incident and Event Services SIEM application is installed by default and can be accessed from the left-hand navigation panel.
Left-hand Navigation Panel > Compliance Control > Incident and Event Services (SIEM) Application  |
|---|
The SIEM Agent is a part of a larger platform and identifies various threats detected by the CE XDR appliance through various types of log files and sends them to the SIEM Server for further analysis.
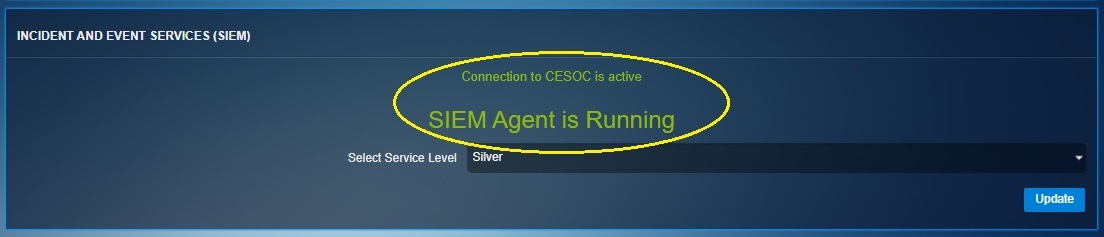
The SIEM Agent Status section shows the current running status of the SIEM Agent and also shows whether the SIEM agent is connected to the Crystal Eye Security Operations Center (CESOC). See the reference screenshot below
There are various types of threat analysis done by the Security Operations Team of Red Piranha for its clients. Threat analysis is offered as a service as per the service level opted by the user under the Incident and Event Services (SIEM) section (see screenshot below).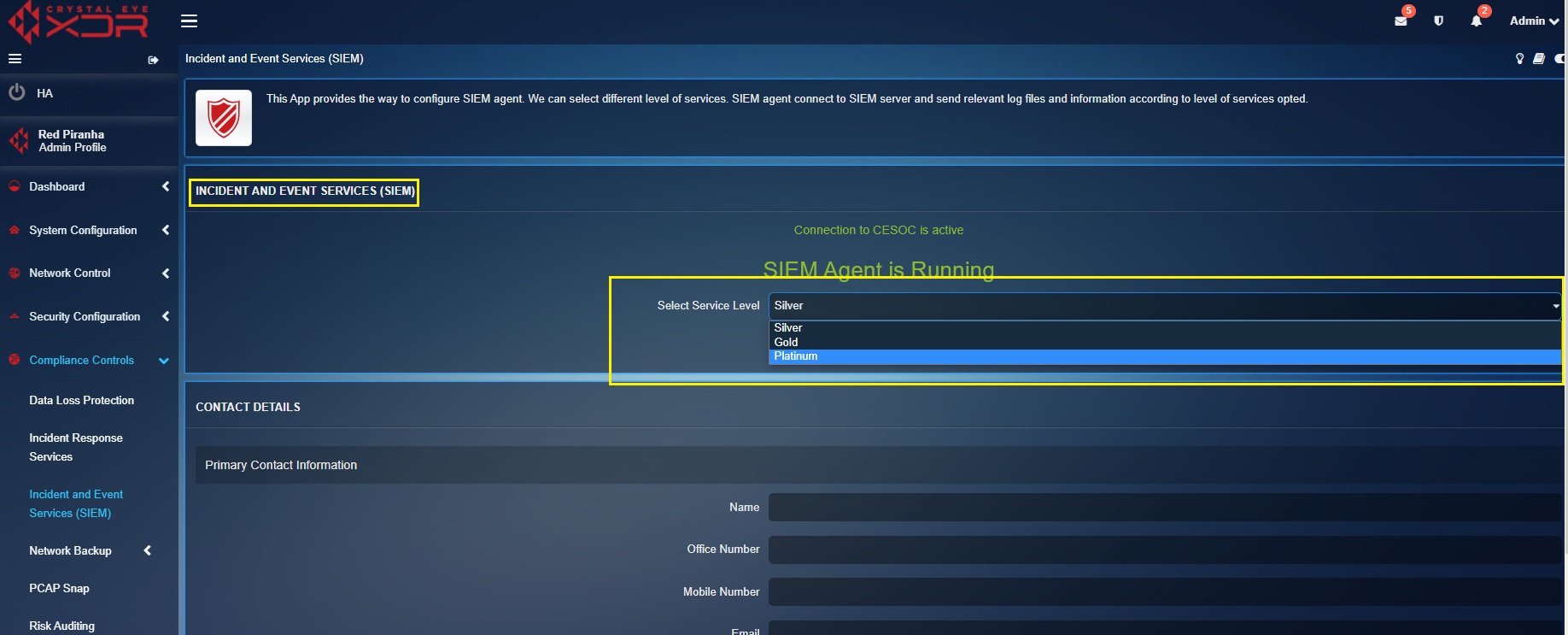
Red Piranha’s Security Operations Team delves into the log files generated from various default apps installed in the CE XDR appliance which is sent by the SIEM agent to the SIEM Server. These log files give insights on the various threats patterns that can pose a risk to the network infrastructure.
The various threat analysis types performed by Red Piranha’s Security Operations Team based on the opted Service Levels are discussed below.
Silver SIEM manages events related to the Availability and Integrity of the CE Asset. This essential tier of service is packaged with all CE series emplacements and included in the Enterprise License.
| App Name | Format | Description |
|---|---|---|
| Integrity Check | syscheck | Checks the system integrity across the file system |
| Mail Log | syslog | Monitors the system internal mail notifications for events. |
| Messages Log | syslog | Monitors Crystal Eye system security messages. |
| Rootkit | rootkit_trojans | Detects possible compromise of the Crystal Eye OS. |
| System Settings | apache | Monitoring GUI access and GUI system audit logs. |
| Forcefield & AAI | syslog | Forcefield provides the CE OS with real-time protection through Automated Actionable Intelligence (AAI). This acquires indicators from local attacks and receives central intelligence from Cyber Threat Alliance (CTA) membership and proactive curation of rules contributed by Red Piranha’s Security Teams. |
| Event Escalation | The local asset Administrator has access to use Human Machine teaming to escalate an Event or Indicator of Compromise (IOC) directly to the Red Piranha SecOps team. This event type are treated at level 3 for analysis and can be used to initiate further threat hunting or an initial Incident investigation, subject to the incident escalation and acceptance process. |
Gold SIEM manages events related to the logging of network level activity.
| App Name | Format | Description |
|---|---|---|
| Content Filter | syslog | Monitors User internet activity and enforcement of policy in the Secure Web Gateway |
| Antivirus | syslog | AV scans web, FTP, mail, & transiting files. |
| Data Loss Prevention (DLP) | syslog | Monitors and block the transit of sensitive files. |
| Secure Web Gateway | syslog | Monitors Web and Email protocols and application layer payloads for viruses and other indicators of compromise. |
| Application Control | syslog | Monitors Alerts from the patented encrypted application allow listing feature |
| AI/ML Anomaly | syslog | Provides essential IDPS anomaly detection for specific attack vector protocols like Kerberos, SMB and SSH and changes in behavior on the deployment related to SID detection. |
Platinum SIEM manages events relating to the collation of TTPs across the data lake. In-depth IDPS analysis includes all preceding logs, bespoke IOT protocols, and can include third party ingestion for custom implementations.
| App Name | Format | Description |
|---|---|---|
| Integrity Check | Syscheck | Checks the system integrity across the file system |
| Mail Log | syslog | Monitors the system internal mail notifications for events. |
| Messages Log | syslog | Monitors Crystal Eye system security messages. |
| Rootkit | rootkit_trojans | Detects possible compromise of the Crystal Eye OS. |
| System Settings | apache | Monitoring GUI access and GUI system audit logs. |
| Forcefield & AAI | syslog | Forcefield provides the CE OS with real-time protection through Automated Actionable Intelligence (AAI). This acquires indicators from local attacks and receives central intelligence from Cyber Threat Alliance (CTA) membership and proactive curation of rules contributed by Red Piranha’s Security Teams. |
| Event Escalation | The local asset Administrator has access to use Human Machine teaming to escalate an Event or Indicator of Compromise (IOC) directly to the Red Piranha SecOps team. This event type are treated at level 3 for analysis and can be used to initiate further threat hunting or an initial Incident investigation, subject to the incident escalation and acceptance process. | |
| Content Filter | syslog | Monitors User internet activity and enforcement of policy in the SWG |
| Antivirus | syslog | AV scans web, FTP, mail, & transiting files. |
| Data Loss (DLP) | syslog | Monitors and block the transit of sensitive files. |
| Secure Gateway | syslog | Monitors Web and Email protocols and application layer payloads for viruses and other indicators of compromise. |
| Application Control | syslog | Monitors Alerts from the patented encrypted application allow listing feature |
| AI/ML Anomaly | syslog | Provides essential IDPS anomaly detection for specific attack vector protocols like Kerberos, SMB and SSH and changes in behavior on the deployment related to SID detection. |
| Intrusion Detection & Prevention System (IDPS) | syslog | The IDPS app performs security scanning at the network level in real-time. All local data is relayed across the SDN for extensive analysis to identify malicious intent through the correlation of Tactics, Techniques, Procedures (TTPs) across all ingested inputs. |
Orchestration of inputs is achieved locally by the CE OS and globally through the Crystal Eye Security Operations Centre (CESOC). Between them is the Service Delivery Network (SDN) which relays intelligence and other service up-dates such as automated patch management. The functionality this provides the CE OS is not limited by the selected service contract. What each tier of managed service relates to is the central monitoring of local intelligence that is relayed to CESOC. What the Silver, Gold, and Platinum service tiers provide is increased oversight and analysis of anomalies detected by the CE OS. Each tier involves progressively more assistance with understanding and managing what the CE OS is detecting.
During the initial deployment, specialised tuning of IDPS settings and rules and other heuristic policy control, will be required for a specific site to achieve the best possible results. Gold and Platinum receive their respective initial tuning as part of the package and receive ongoing tuning annually for Gold, and Quarterly for Platinum. All service contracts are automatically subscribed to weekly Threat Intelligence reports outlining the latest curated rules to target the Tactics, Techniques and Procedures (TTPs) of threat actors.