IPSec VPN
Crystal Eye XDR’s IPSec VPN application enables administrators to create encrypted tunnels between two sites further enabling secure communications. These tunnels can be configured to support IPSec Site-to-Site network connections and the sole aim of using IPSec VPN is to establish secure connections between two networks (example two office branches).
The CE XDR’s IPsec VPN has in-built default IPsec policy configurations that ensures strong cryptography. The latest IPsec policies in Crystal Eye 4.0 have all the unused or non-compliant cryptographic suits removed which makes IPsec VPN communications secure.
The current version of the IPsec VPN is compatible with the High Availability feature ensuring undisruptive accessibility through IPsec VPN tunnels established between 2 sites.
The IPsec VPN is not a default application. It needs to be installed and configured from Marketplace in the left-hand navigation panel.
Left-hand Navigation Panel > Network Control > SD WAN > IPSec VPN  |
|---|
An IPSec Site-to-Site VPN allows offices in multiple fixed locations to establish secure connections with each other over a public network such as the internet. IPSec Site-to-Site VPN extends the company’s network, making computer resources from one location available to employees at other locations. The best example of a company that needs an IPSec Site-to-Site VPN could be a growing cooperation with dozens of branch offices across the globe. If a company has one or more remote locations that they wish to join in a single private network, they can create an intranet VPN using the IPsec VPN application of CE XDR to connect each separate LAN to a single WAN.
IPSec Site-to-Site VPN can be explained with the help of the following sample setup:
Before starting with the configuration of an IPSec Site-to-Site VPN tunnel, two working Crystal Eye XDR appliances are required or (one CE and any other device that supports IPSec Site-to-Site VPN) with a unique LAN IP subnet for each side of the connection (LAN subnets must be different from the LAN subnets of the remote network). Another requirement is that the hosts connected to the CE XDR must be connected to the internet.
For the sample configuration, we shall use two Crystal Eye XDR appliances to stimulate an IPSec site-to-site tunnel, with the following network configurations:
| Configuration | Site A | Site B |
|---|---|---|
| WAN IP | 173.208.246.243/29 | 173.208.246.244/29 |
| LAN 1 | 10.10.1.1/24 | 10.20.1.1/24 |
| LAN1_VLAN_21 | 10.10.2.1/24 | 10.20.2.1/24 |
| LAN 2 | 10.16.1.1/24 | 10.17.1.1/24 |
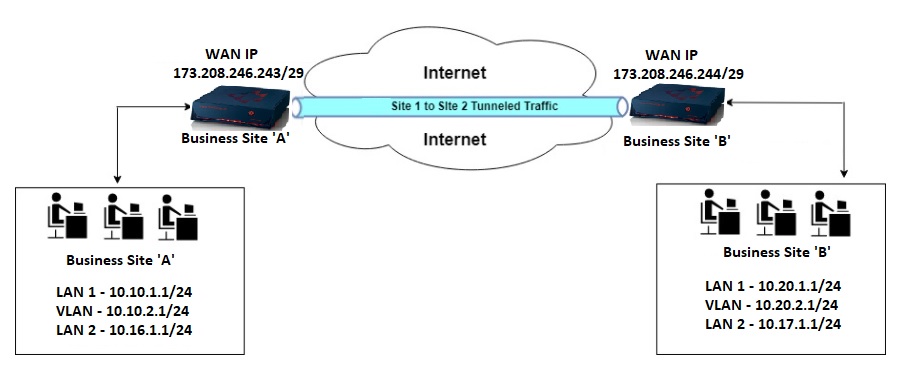
In the diagram above, the WAN IP of CE XDR in Business Site ‘A’ is 173.208.246.243/29 and the WAN IP of the CE XDR in Business Site ‘B’ is 173.208.246.244/29. Both these sites are connected to each other through an IPSec Site-to-Site VPN tunnel.
| Business Site ‘A’ CE XDR Configuration for IPsec VPN |
|---|
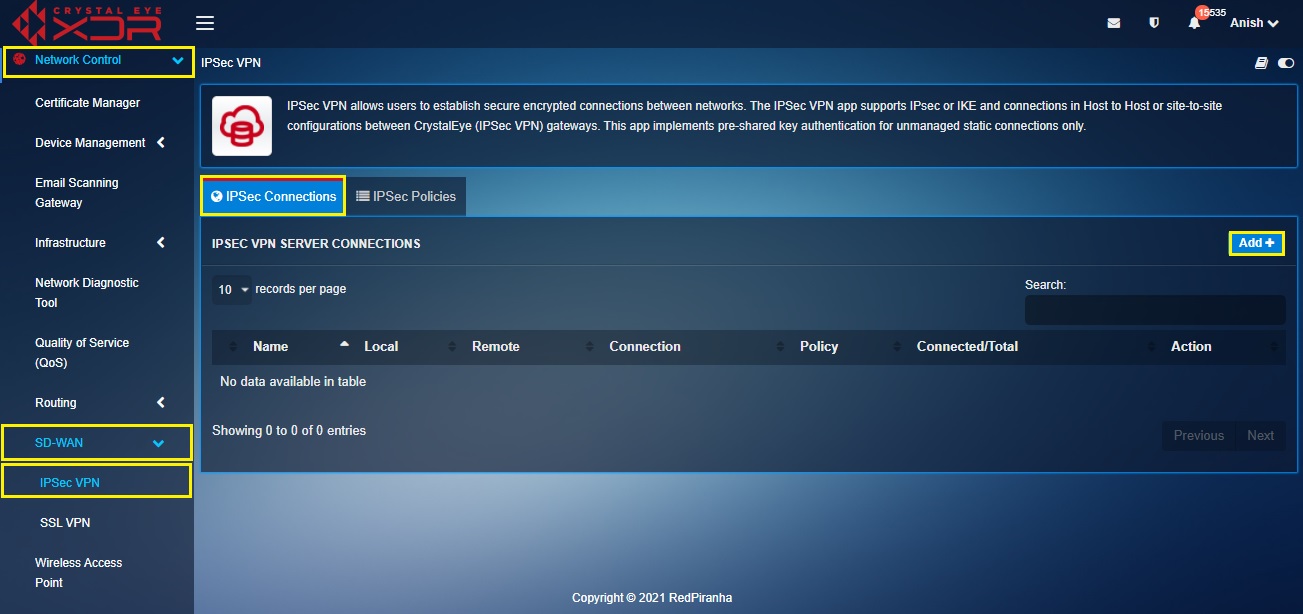
Step 1: In the IPsec VPN application page, click the Add button on the top-corner of the IPsec VPN Server Connections section.
Step 2: You will see the Add New IPsec Connection page. Enter the desired Connection Name in the textbox in the General Settings section. In our scenario we have named the connection as S2S_S1_S2.
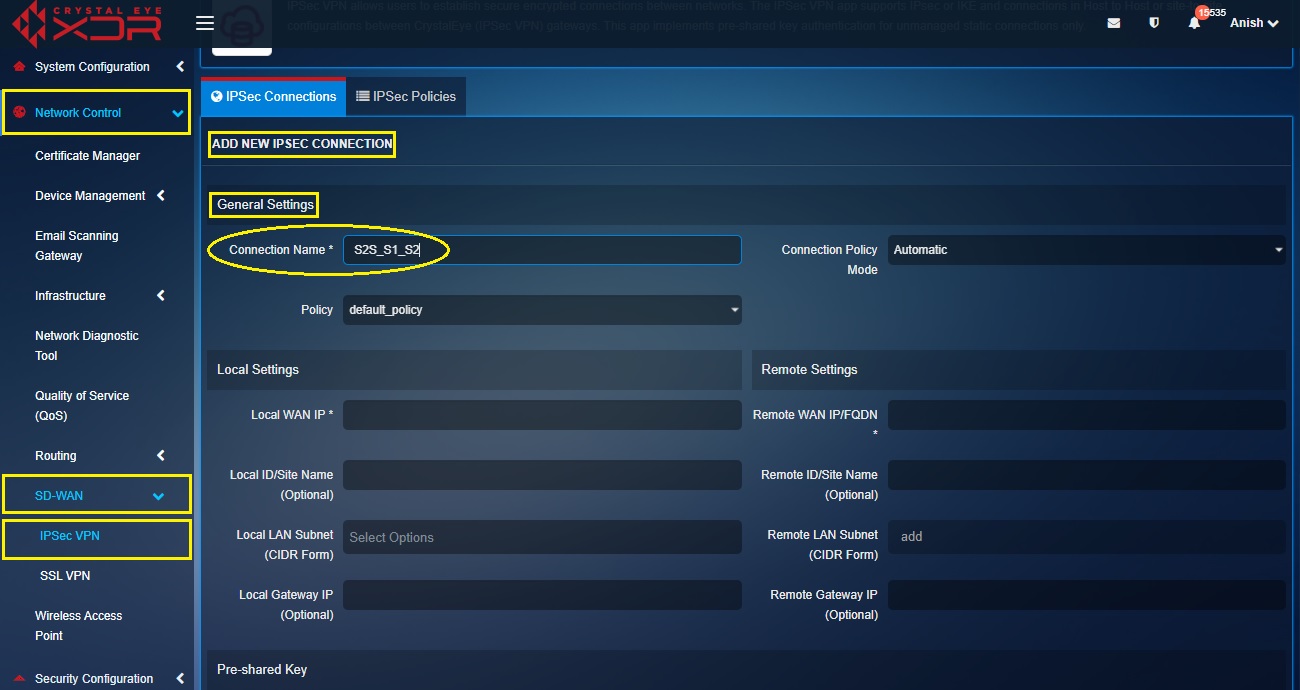
Step 3: Select the Connection Policy Mode as Automatic and the Policy type as default_policy from their respective dropdowns.
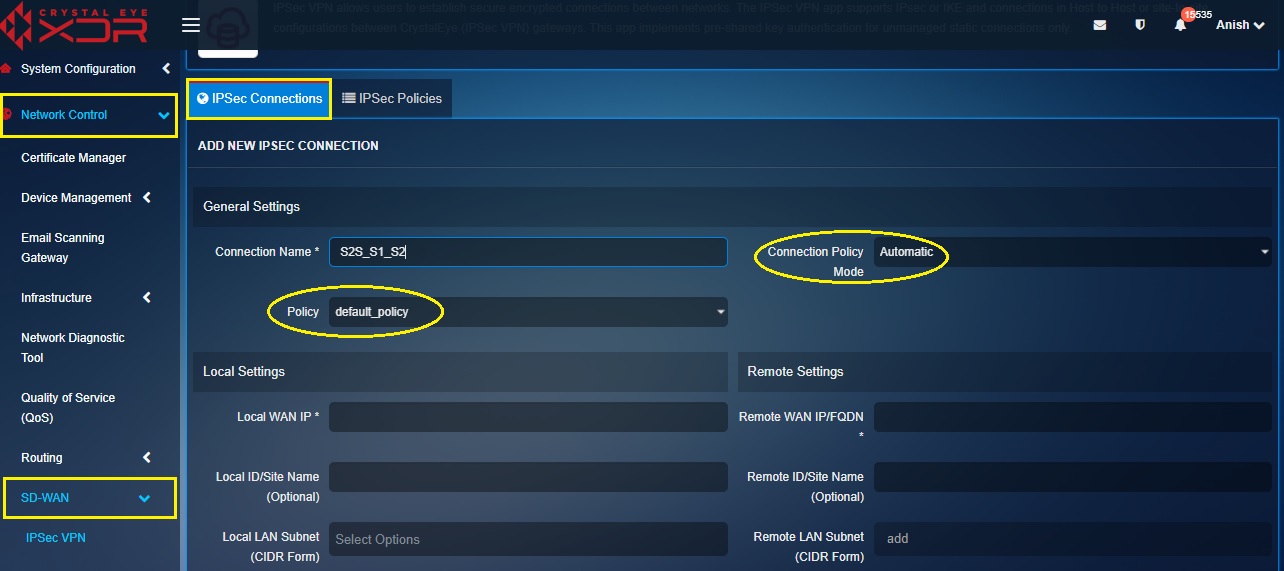
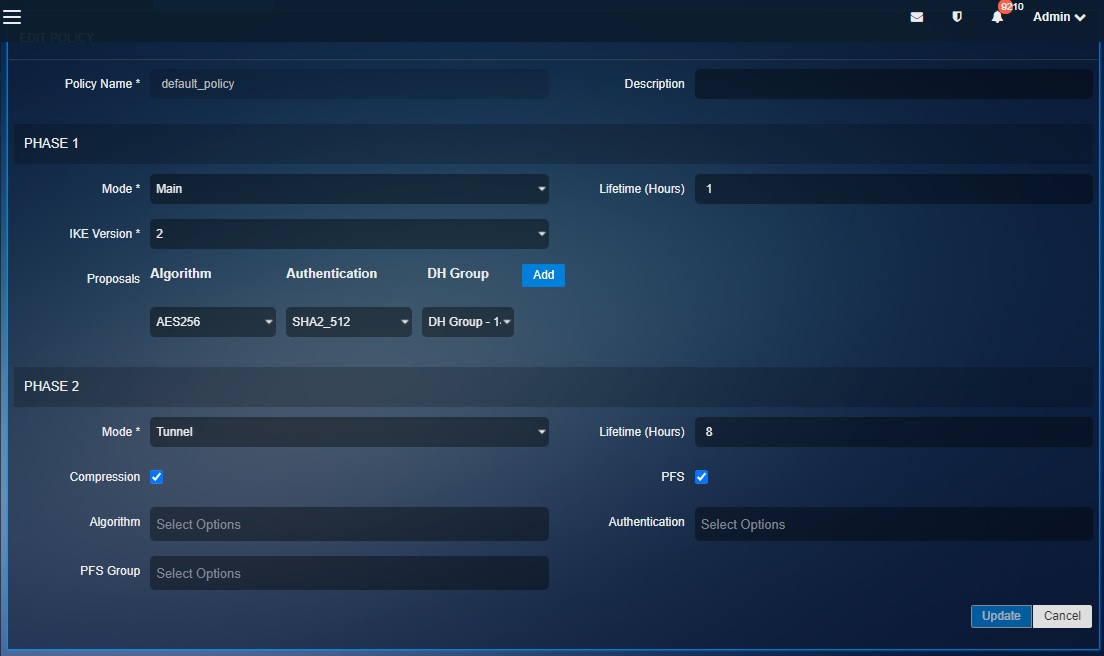
Note: The Crystal Eye XDR offers two default IPsec policies defining the security parameters much required for a negotiation of a VPN tunnel to happen. These two default policies named, default_policy_ikev1 and default_policy have been set distinctly (refer to the screenshots below to know the settings of the two default IPsec policies) 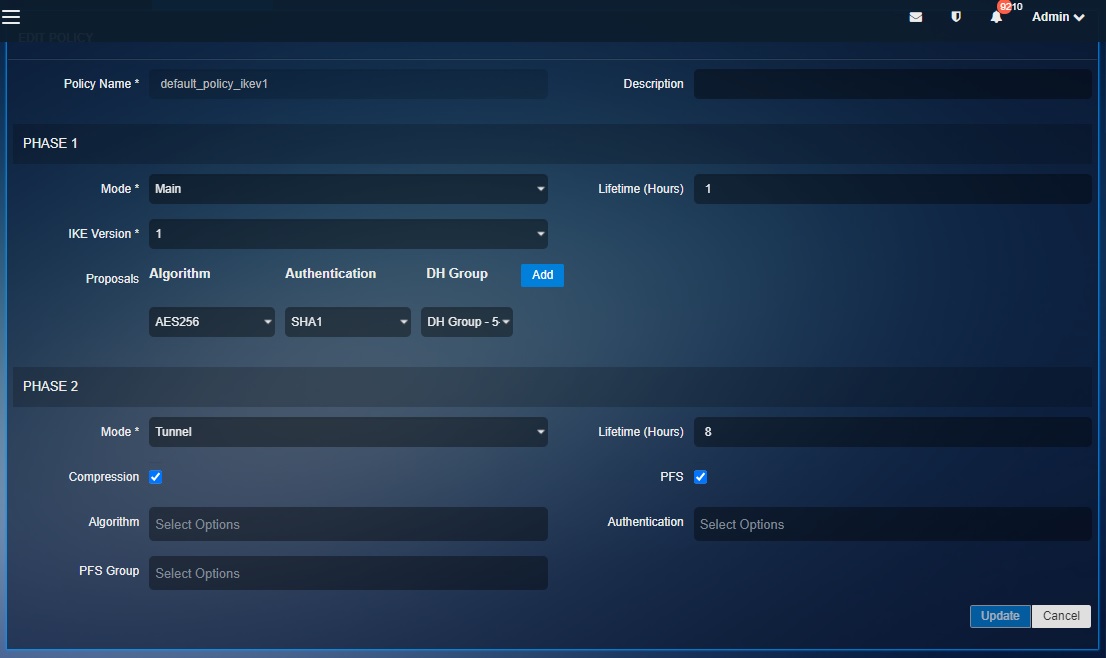
Step 4: Select the WAN1 IP address 173.208.246.243 from the Local WAN IP dropdown under the Local Settings section and enter the Remote WAN IP (in FQDN format) under the Remote Settings section.
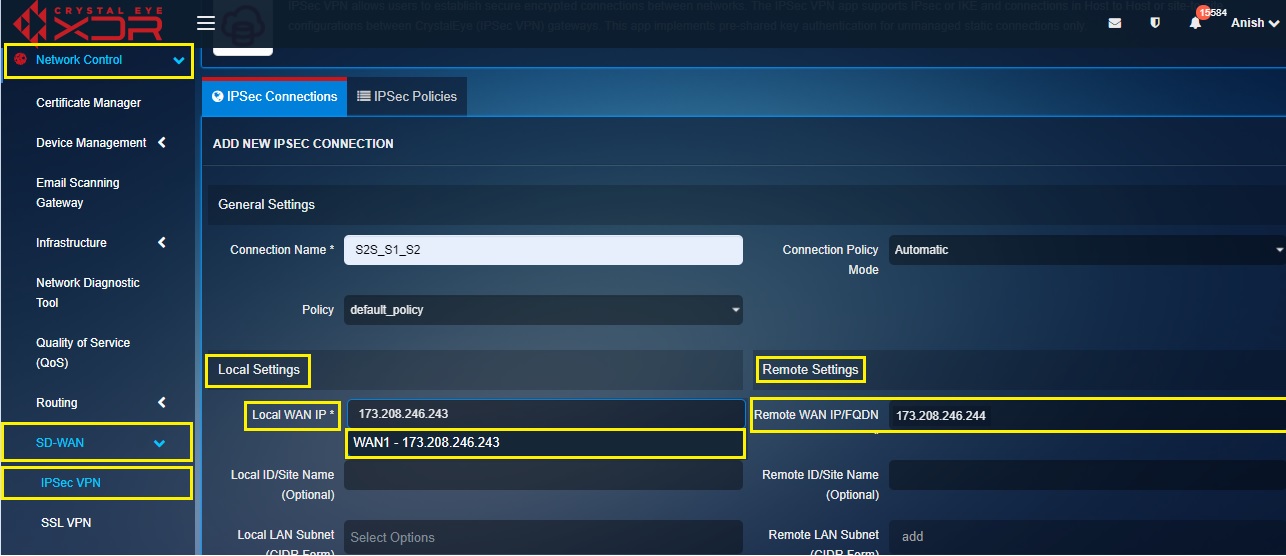
Note: Local Settings section relates to configurations related to the CE XDR appliance deployed as a gateway endpoint in Business Site ‘A’ and Remote Settings refers to the configs related to the CE XDR appliance deployed as a gateway endpoint in Business Site ‘B’.
Step 5: Enter a unique ID for both the CE XDR’s with a prefix ‘@’ in the Local ID/Site Name text box and the Remote ID/Site Name text box.
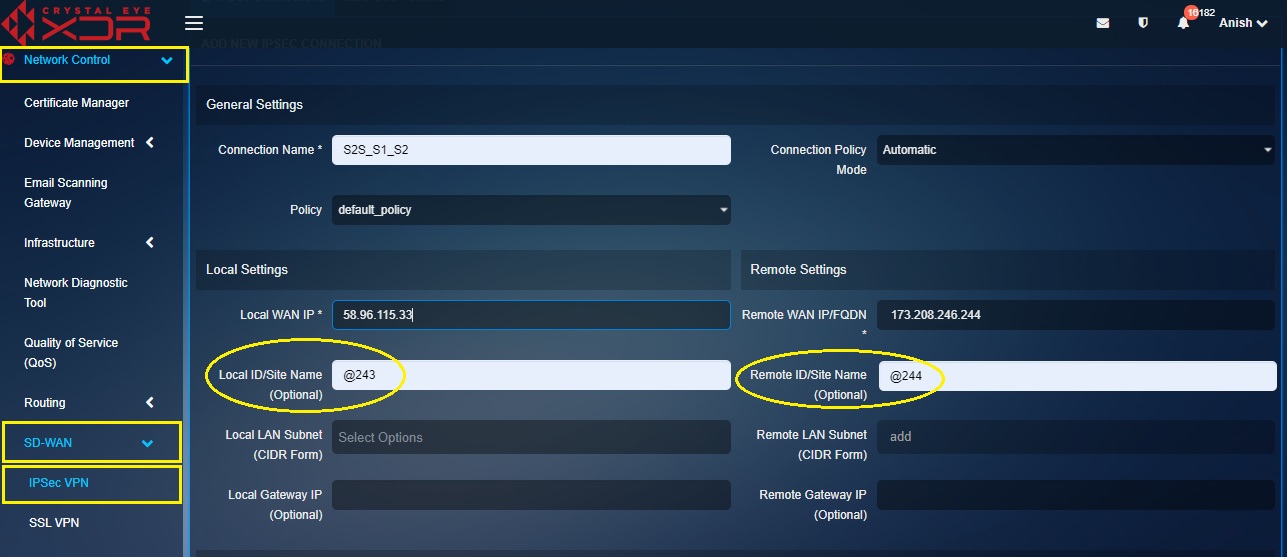
Note: In our scenario, Local ID/Site Name is @243 and Remote ID/Site Name is @244.
Step 6: Select the subnets of the CE XDR deployed in Business Site ‘A’ in the Local LAN Subnet text box and consequently select the subnets of the CE XDR deployed in Business Site ‘B’ in the Remote LAN Subnet text box.
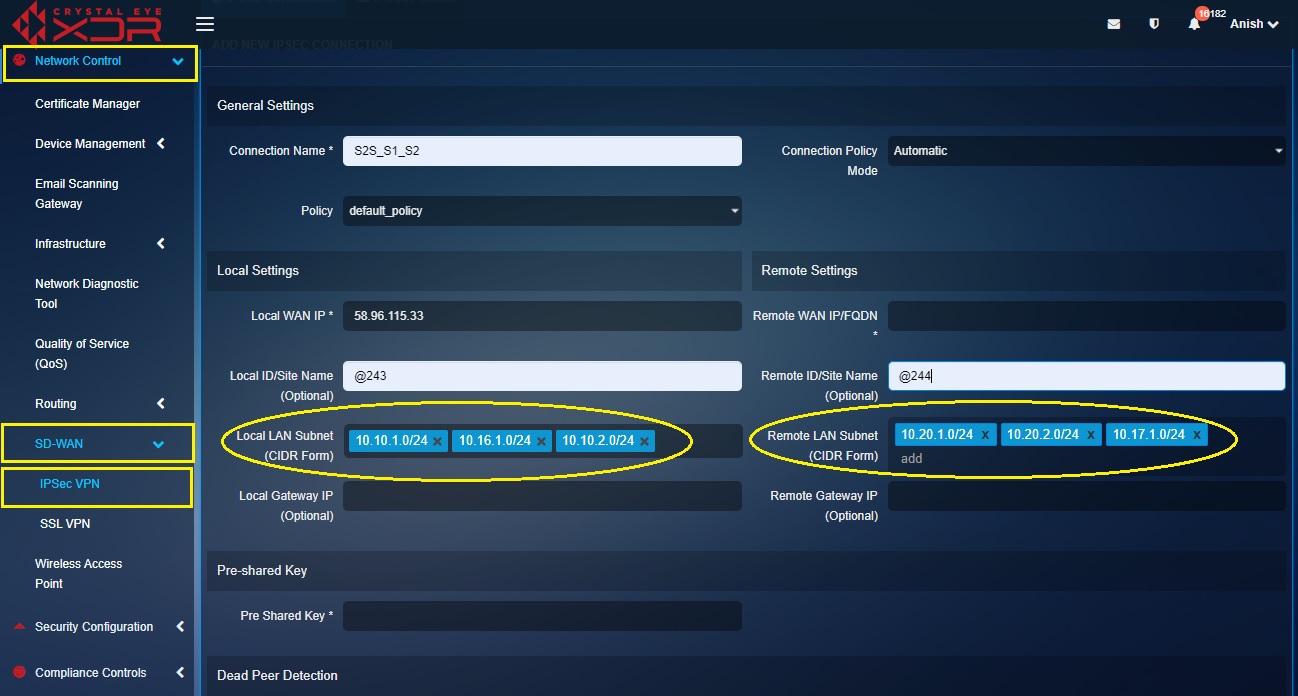
Step 7: Enter the Pre-shared Key in the text box and click the Update button.
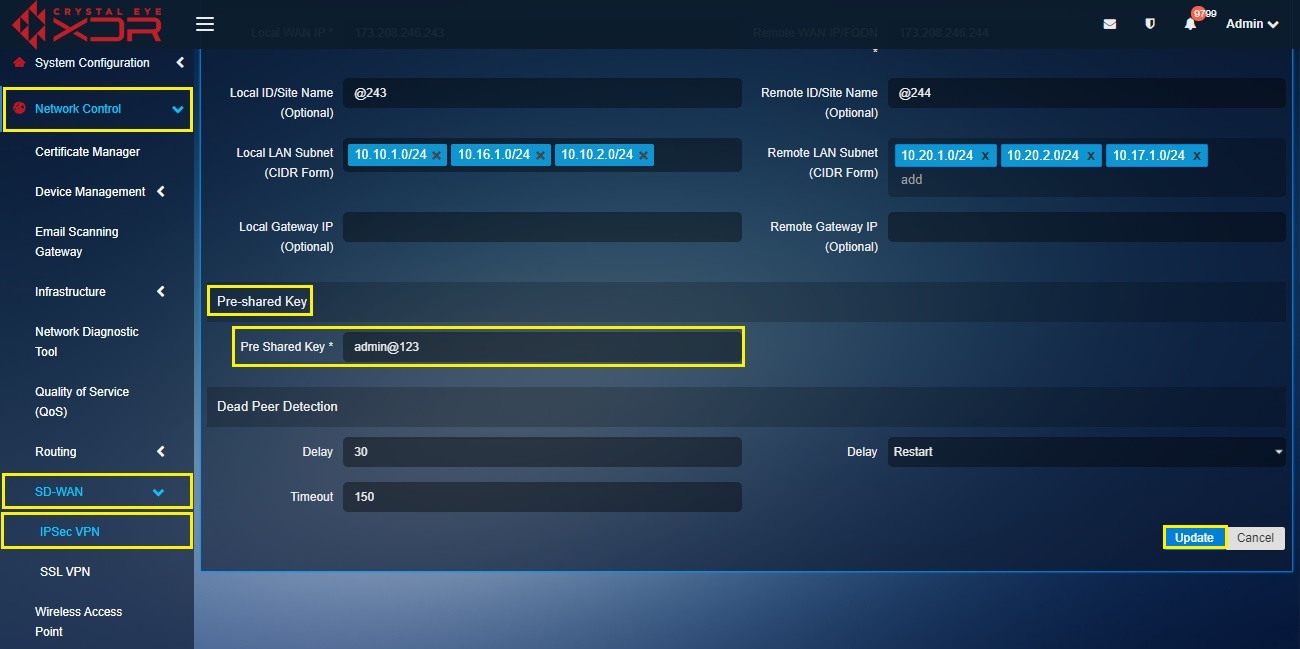
| Business Site ‘B’ CE XDR Configuration for IPsec VPN |
|---|
Step 8: Configure Business Site ‘B’ CE XDR to match the settings mentioned below in the screenshot. Please note that the procedure mentioned from Step 1 to Step 8 can be referred to while configuring IPsec VPN on the Business Site ‘B’ CE XDR.
General Settings, Local Settings, and Remote Settings:
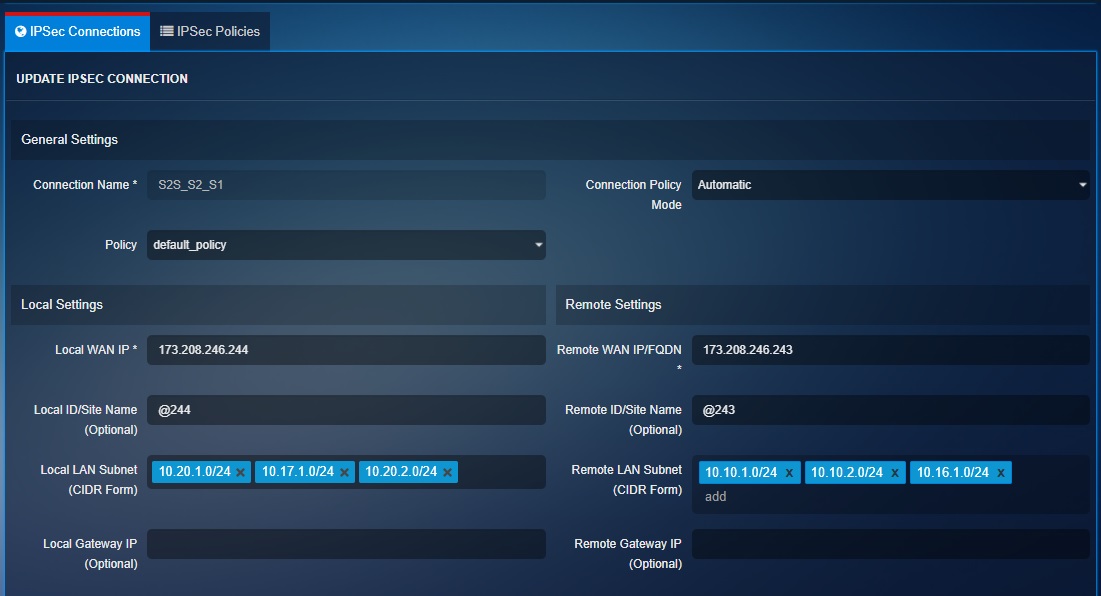
Pre-shared Key and Dead Peer Detection:
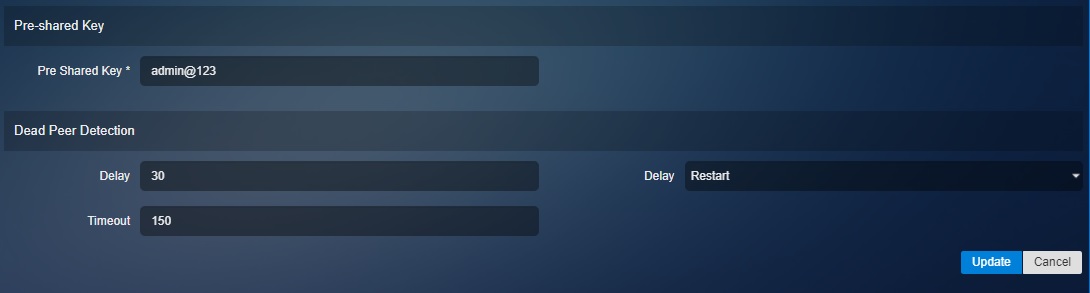
After updating the settings mentioned from Step 1 to Step 8 you will be able to see the IPsec connection up and running in the IPsec VPN Server Connections section.
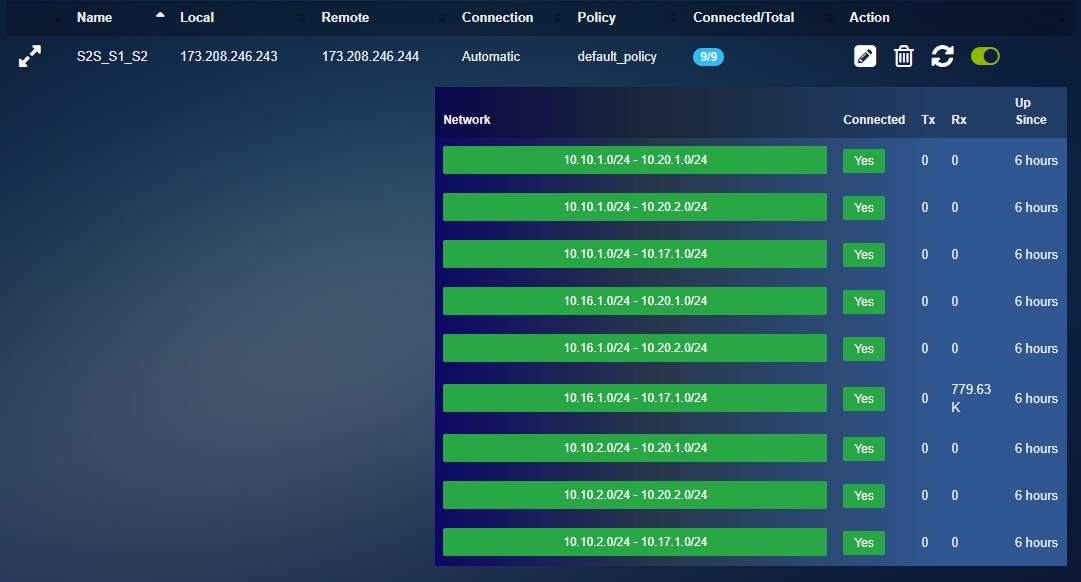
Business Site ‘A’ CE XDR IPsec VPN Server Connections:
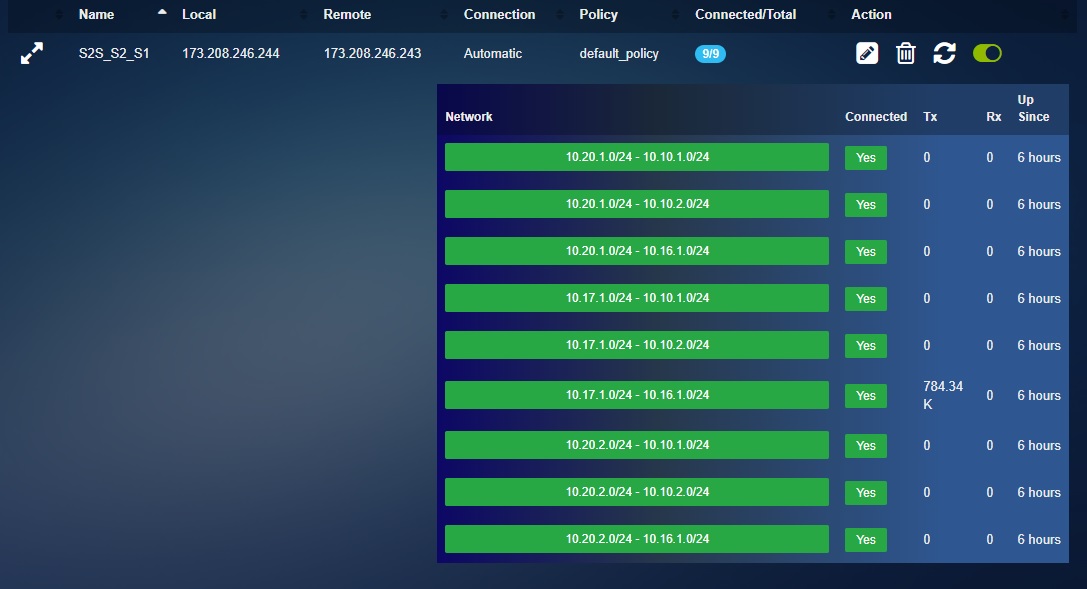
Business Site ‘B’ CE XDR IPsec VPN Server Connections:
The Crystal Eye XDR’s IPsec VPN application has elaborated features that allow users to create custom IPsec VPN policies. These IPsec policies play a vital role in outlining specific recommendations and best practices for securing the IPsec VPN connections.
The encryption methodology configured allows the IPsec tunnel to provide security functions such as ‘privacy’. Some of the other security functions offered by CE XDR’s IPsec VPN are providing the required integrity of the content through data authentication.
It is imperative to configure a strong cryptography on the IPsec VPN connection so that the tunnel not at risk and that the data confidentiality is not lost.
The Crystal Eye XDR offers two default IPsec policies that the user can choose while configuring site-to-site IPsec VPN.
The following screenshots show the settings of the two default IPsec policies in CE XDR:
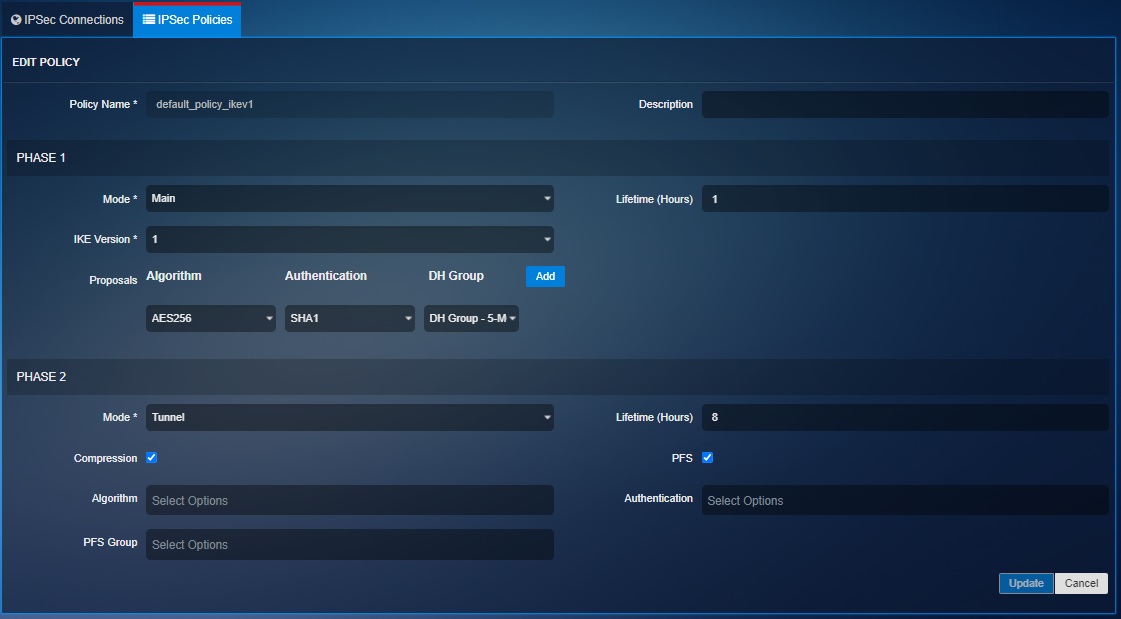
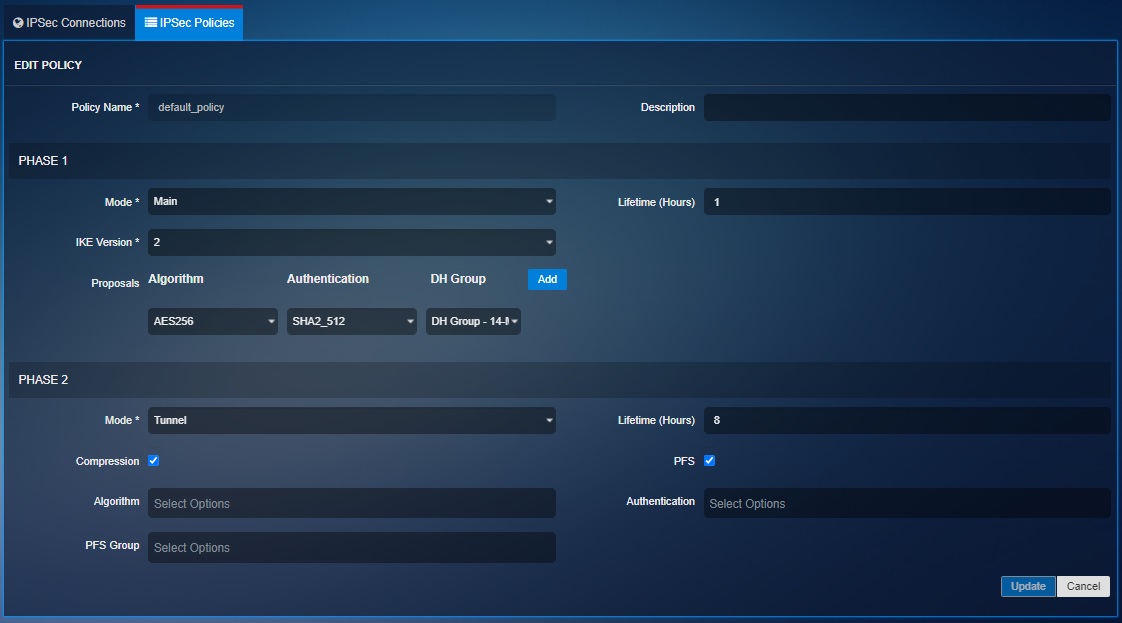
Main Mode: The main mode can only be used if both the CE XDR appliances on either side of the IPsec VPN tunnel has a static IP address. The primary function of the main mode feature is to identify and validate the IP address and the gateway ID assigned to each CE XDR appliance.
Aggressive Mode: The aggressive mode is considered less secure than the main mode mainly due to the fact that there are fewer exchanges between the CE XDR’s deployed at both ends of the IPsec VPN tunnel. However, the fewer exchanges in an ongoing IPsec VPN connection running on aggressive mode also makes it faster. Unlike main mode the identity of the CE XDR is not ensured and henceforth the exchange mainly relies on the ID types used in the exchange by both CE XDR’s deployed as a gateway.
IMPORTANT: It’s a long-known fact that aggressive mode is less secure than main mode (also described in CVE-2002-1623).
Lifetime (Hours): The amount of time until the Phase 1 Security Association expires
IKE Version: The CE XDR IPsec VPN policies offers both IKEv1 and IKEv2
Algorithm: The type of encryption algorithm (3DES, or AES) and key length
Authentication: The type of authentication (SHA-2, SHA-1, or MD5)
DH Group: The Diffie-Hellman key group
Tunnel Mode: The tunnel mode allows traffic encryption between two CE XDR’s deployed as a gateway on both sides of the tunnel. This mode is widely used in the scenario of Site-to-Site IPsec VPN where two CE XDR’s is connected over the internet via IPsec VPN.
Transport Mode: This mode is designed to support end-to-end IPsec VPN communications such as comms between a server and a client. Transport mode is widely used to support host-to-host IPsec VPN identical to a scenario where we have a remote desktop session from a workstation to a server (given that both the hosts are behind two CE XDR’s)
Lifetime (hours): The Lifetime (hours) option allows users to assign a specific key expiration interval that basically ensures that the phase 2 keys change after regular intervals. This configuration is done to reduce the time window available to mount an attack on the key. There is a higher degree of risks involved with the phase 2 encryption key being used for longer periods. The default settings of Lifetime (hours) of phase 2 is 8 hours.
PFS: It is recommended to enable PFS to ensure safety of the data transferred via IPsec VPN. Please note that PFS must be enabled in both the CE XDR appliances on both sides of the IPsec VPN tunnel and that identical DH-groups must be assigned at both ends.
Algorithm: Cryptographic algorithm keeps the data confidential. You can select DES, 3DES, or AES, or AES-CTR. AES variants are the only secure options. It is recommended not to use outdated cryptographic algorithms such as Triple DES (3DES).
Authentication: Available options for authentication are MD5, SHA1, SHA2-256, SHA2-284 and SHA2-512. As per CNSSP 15 as of June 2020 the recommended authentication is SHA-384.