Crystal Eye XDR Configuration Best Practices
At Red Piranha, we came up with a simple concept: a holistic security solution that works. We have developed the most exhaustive and effective security controls available and have roped in the best minds to achieve this. The best practice documentation has been developed to aid administrators configure the Crystal Eye XDR in the most favourable way that would help to protect, detect, and respond to cyber-attacks. This section of the manual will offer you guidance to roll out a defence in-depth strategy by setting CE XDR policies to keep up with ever-changing threat landscape.
Below are some of the recommended best practices that can be referred to while configuring the CE XDR:
Efficient Management of the Crystal Eye XDR
The Crystal Eye XDR being the focal point for the network and end-point security requires a good understanding of the best practices for its commissioning. Some of the general tasks that constitutes the major chunk of CE XDR’s management are upgrading, on-going monitoring, and incident management.
The task of managing the CE XDR must not be underestimated and considerable number of human resources must be allocated for this task.
CE XDR can be easily mis-configured if its management is not taken seriously having an adverse effect on the network and the devices in it.
Henceforth, its recommended to consider the following management tasks before and after deploying the Crystal Eye XDR:
-
Documentation of the CE XDR access control list & advanced firewall rules: Documenting the access control list of the CE XDR must be given due importance in addition to clearly enumerating each firewall rule and determining its interdependencies and security considerations.
-
Validating the business case on regular intervals: The business case taken into consideration while deploying the CE XDR must be validated at frequent intervals to ensure that the security controls are in place.
-
Adherence to the change management policy while changing the CE XDR configurations: A formal change management policy must be adhered to in manage any change requests of the CE XDR configurations. A list of the change management tasks directed towards changing CE XDR configurations must be created after closely reviewing the change management policies of the organization.
-
Monitoring firewall logs and IDPS events: A dedicated personnel or a team must be constituted and assigned to monitor the firewall logs and the IDPS events that pops-up on the security dashboard of the CE XDR.
-
Updates & Upgrades: The CE XDR management team must take into consideration of the fact that all new updates are installed in the appliance. To ensure that this process is automated its highly recommended to enable the automated updates feature of the CE XDR from the Software Updates application.
-
Defining a Robust Incident Response Plan: It is imperative to understand the importance of constituting a flawless incident response plan keeping in mind the organizations business use case. An Incident Response Plan is the emergency response plan that is formulated to enumerate the list of things that will be done to address suspected or actual incidents. The first line of response might include possible disconnection of the infected devices or subnets of the network. Not just this, the incident response plan also provides a detailed description of the re-engagement process which might include re-activating the infected systems after they cleaned -up and patched.
Crystal Eye’s Managed Detection and Response application can be considered as an excellent tool to capture events at the endpoints and send the relevant data back to the centralised XDR data lake to correlate and report on relevant security activity and incidents. This app also forms the End-point Detection and response (EDR) of the entire CE XDR platform.
Configuration Backup
Ensure that the CE XDR current configuration backup is done before making any major changes to its configuration. This should be practiced avoiding any misconfigurations of the CE XDR. This can essentially be achieved using the configuration backup and restore application and the bare-metal backup application.
Encrypted Configuration Backup
Always consider taking an encrypted backup of CE XDR configurations as Its an extra security measure for enhanced secrecy of the configurations. Encrypted configuration backup’s can be taken using the configuration backup and restore application.
Adoption of a Robust Role-based administration policy of the CE XDR
A Robust role-based CE XDR administration policy must be created and implemented using the ‘administrator application’. This application gives the ability to admins to ensure restricted access to certain areas of the XDR and provide read/write access to certain users according to the designated role. The policy of Least Privilege must be adhered to so that the user is given access rights in accordance with their functions.
Note: This feature is only configurable when the CE XDR administrator is logged in as a root user.
Avoiding Single Point of Failure on the CE XDR Network
The High Availability feature of the CE XDR must be actively used to ensure continuity of services regardless of the possible node failures in the network.
Crystal Eye XDR’s high-availability feature is designed to place two firewalls such that the primary CE XDR synchronizes its configuration with the secondary CE XDR preventing a single point of failure on the network. Organizations must seek to improve the quality of the service and aim for an increment of the availability of their resources through the High Availability feature.
Note: HA is only configurable in CE XDR models (series 20 or greater) which are of the same series. Eg: HA can be configured between 2 CE XDR series 20.
Adherence to a Change Management Policy
Change management here refers to a formal process followed and implemented for making changes to the CE XDR configurations.
Crystal Eye XDR administrators must be aware of the latest available system software versions available for upgrades. This can be found at the system software section of the software updates application.
It is advisable to ensure that the automatic updates feature is enabled in the software updates application. This would allow automatic integration of the CE XDR appliance with the any available feature release with improved or optimized functionality.
Identifying Unknown/Rogue Devices Connected to your Network
A standard process must be followed to ensure that unknown or a rogue device are identified and immediately revoked over the CE XDR network.
It is advisable to scan your CE XDR network on a regular basis to identify unknown devices in your network. The best way of checking if the device belongs to your network is by mapping all your devices and assigning it a nickname using the network map application. The ones which are new to the network can then be easily identified by the CE XDR administrator as it would show up under the unmapped device category of the network map application.
Updating the default Wi-Fi SSID and updating your Wi-Fi password with a strong one is considered as an excellent approach to further strengthen network security.
Formulating a robust Internet Gateway Security Policy
It’s important that a comprehensive internet gateway security policy is configured on the CE XDR with security goals such as minimizing the hacker’s ability to attack the network. This would essentially mean to reduce the chances of network intrusion and if there is a network breach the presence of the attacker must be identified.
Achieving these security goals can be made possible by following best practices while configuring gateway security policies.
Your internet gateway security policy can be implemented by having a four-dimensional approach mentioned below:
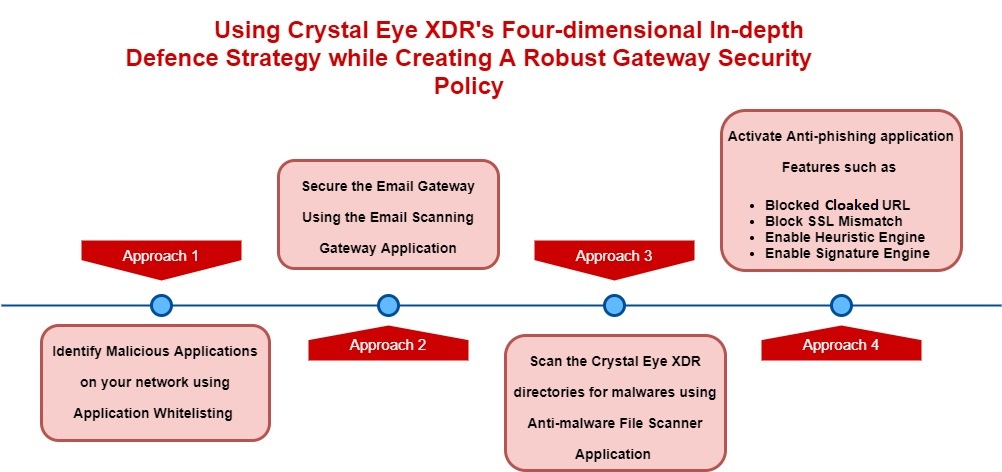
-
Identify Malicious Applications on your network: CE XDR features such as application whitelisting can be used to enforce application-based rules to block any malicious application in the network and allow access to whitelisted applications.
-
Securing the Email Gateway: Configuring the Email Scanning Gateway application would protect users behind the CE XDR from email related attacks such as phishing. The scanning functionality of the application has been designed to eliminate any attached malicious files and then let the email pass through to reach the desired destination address.
-
Scanning the CE XDR directories for malwares: The anti-malware file scanner app scans various directories of the Crystal Eye XDR for malwares. This powerful application has been designed to scan CE XDR internal directories such as home directory, network file share directory and web proxy cache. The infected files are quarantined and can be seen in the Quarantine Section. The flagged files which are quarantined can be granted access to the system using the whitelisting functionality.
-
Anti-phishing application: The Anti-phishing application blocks the user from visiting sites that are known to steal credentials and spread malware. The platform makes use of signature-based and heuristic mechanisms from automatically updated rules to identify malicious URLs. The platform intelligently scans URL’s, and the scanning engine ensures that cryptographic certificates are valid and match the host as claimed. The scanning process is also aimed at detecting links that are cloaked to deceive end users.
Segregate the CE XDR network into Different Zones
The Crystal Eye XDR network must be segregated to various zones so that any internet-facing servers are deployed in a separate zone different from the LAN network. As a rule of thumb, all internet facing servers must be placed in the DMZ Zone. Crystal Eye XDR advanced firewall rules must be configured to ensure that the traffic from DMZ to the LAN is blocked.
It’s recommended to further segment LAN Zones by creating more subnets and then assign these subnets to sperate LAN Zones. The traffic rules of the advanced firewall application must then be configured to manage the traffic flowing from these subnets assigned to the LAN Zone.
Why Segregate Networks?
Network segregation is one of the fundamental best practices that must be followed to ensure that attackers don’t treat the entire network as a low hanging fruit while hacking it. The goal here is to restrict explicit access to confidential information, services, and hosts.
Below is a perfect example how a segregated or a non-segregated network would respond to network intrusion by a malicious actor:
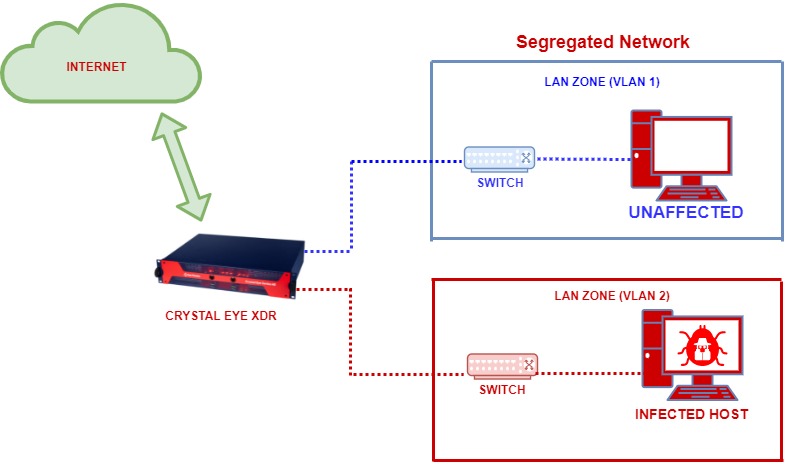
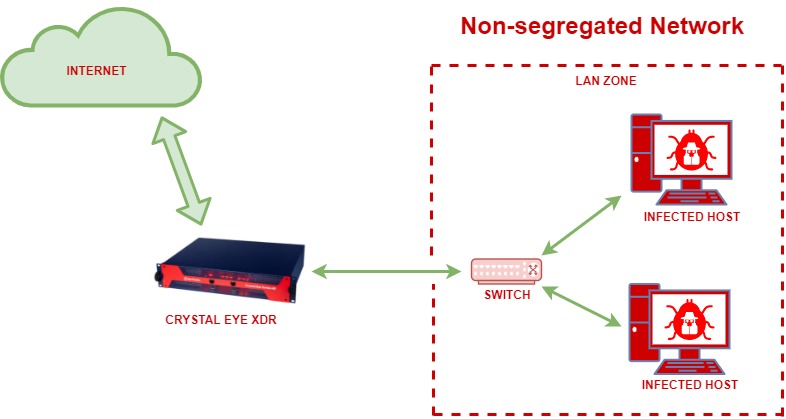
Suggested Firewall Security Zone Segregation
Apply IDPS & Web Filtering Policies to Traffic Flowing from Segregated Networks
It is recommended to segregate the network into different zones and apply IDPS policies and content filter policies to it using the Advanced Firewall application of the Crystal Eye XDR. The Advanced Firewall application can be used to create custom zones and then specific IDPS and content filtering traffic rules can be applied on the traffic flowing across these zones.
Create Schedules for Internet Usage & Web Filtering Traffic Rules
Based on the requirements, organizations must consider creating schedules for internet usage and the time slot for enforcing web filtering policies.
For example, less stringent content filter policies would need to be enforced to a marketing team working in the day shift as compared to rules set for the marketing team working during the evening shift. The policies can be segregated as per the time slot using the schedule feature of the advanced firewall application.
Allow Only Authenticated Users to Access the Internet from LAN Zone
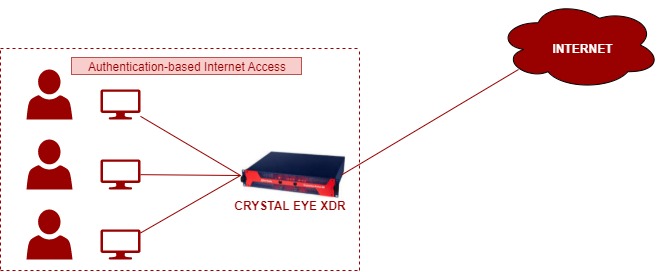
A zero-trust network architecture can essentially be implemented at the CE XDR network user’s level by allowing only authenticated users to access the Internet from the LAN Zone. Authentication-based content filter feature of the CE XDR can be activated for all outgoing traffic from LAN to WAN. Once this feature is activated the users connected to the LAN interface trying to access the internet will be prompted to enter user credentials.
Protecting the CE XDR GUI from Unauthorized Intrusion Attempts
The Crystal Eye XDR’s in-built self-defence mechanism called ‘forcefield’ has advanced capabilities to automatically block any unauthorised intrusion attempts targeted towards the CE XDR.
It is recommended to retain the default global properties configurations that bans a malicious actor trying to break into the CE XDR for 168 hours for a maximum failed attempt of 3 times.
The forefield feature of the CE XDR is designed to handle three types of attacks namely, Postfix-SASL attacks, SSHD attacks and Webconfig attacks. The rules to stop these attacks must be always activated/enabled in the Rules section of the forcefield application.
Configure the Automatic Software Updates Feature of the CE XDR
Always ensure that the Automatic Software Updates feature of the CE XDR is activated so that the CE XDR appliance receives the latest updates pushed through the Red Piranha’s Service Distribution Network (SDN).
Create a Comprehensive Internet Usage Policy and Implement it Using Web Filtering & Protocol Filtering
A comprehensive internet usage policy must be formulated to ensure that the users in the CE XDR network are aware of the rules and guidelines related to the appropriate use of company assets. The CE XDR’s web filtering and protocol filtering capabilities can be best used to compliment the internet usage policies.
The following recommended settings related to web filtering and protocol filtering of the CE XDR can be used to compliment a comprehensive internet usage policy:
Global Exception IPs: The Exception IPs feature of Crystal Eye XDR’s content filter application provides the leverage for administrators to quickly permit IPs and exclude them from various block categories.
Global Banned IPs: The Banned IPs feature of Crystal Eye’s content filter would block the listed host IPs from accessing the internet.
Detailed Logging: The detailed logging features can be activated to monitor the content filter logs and then fine tune the implemented content filter policies as per the findings.
Blacklisting Website Categories: The Blacklist feature allows the Crystal Eye XDR administrator to blacklist all websites related to a specific subject for example, abortion, alcohol, cell phone and a lot more.
Blocking Content Consisting of a Specific Phrase: There are a set of Phrase List categories that can be selected to filter relevant browsing content. Once this feature is activated, the Crystal Eye XDR would scan the browsing content for the selected phrase list based on the sensitivity levels opted in the Dynamic Scan Sensitivity section. The content filter application calculates a score for each web page based on the number of times a forbidden phrase is detected and then blocks the content accordingly.
Blocking Specific File Extensions: This content filtering feature can be used to ban specific file extensions so that there are fewer chances of malicious codes and viruses being downloaded by the end users in the Crystal Eye network.
Banning a Specific Website: The Banned Sites feature of the Content Filter application is used to block certain websites manually regardless of its content.
Application filtering: This feature is used to block various applications in the Crystal Eye XDR network. There is an exhaustive list of applications that can be banned. The applications are classified under various categories such as Arts & Entertainment, Mail, Messaging and Forums, News, File Sharing, Shopping, social media, and Technology.
Protocol Filtering: The major functionality of the Protocol Filter App is to ensure that it blocks restricted traffic to enter the network. The app blocks a range of protocols, regardless of which website or application the protocol is used to communicate with. The protocols are identified by traffic contents and by the port and traffic type.
Enable SSL Decryption to Ensure both HTTP and HTTPS Traffic is Scanned by the Content Filter application
The Crystal Eye XDR runs on Transparent mode by default which also points out to the fact that the CE XDR appliance scans only HTTP content by default.
However, to extend the scanning capabilities of CE XDR’s content filter application to https traffic, the content filter mode would have to be changed to Transparent_SSL mode or Explicit_SSL mode.
Reduction of the IPsec VPN gateway attack surface
Strict traffic filtering rules must be created and implemented to mitigate the vulnerabilities posed by IPsec VPNs. One of the reasons for such a stringency is the fact that IPsec VPN is directly accessible from the internet. Access to UDP port 500, UDP port 4500 and ESP must be limited.
Reviewing the Cryptographic Algorithms of the IPsec VPN Connection
The Crystal Eye XDR’s IPsec VPN is designed to accommodate a robust Internet Key Exchange (IKE) policy and IPsec Policy. These policies define the baseline as to how the established IPsec tunnel will negotiate phase 1 and phase 2 negotiations. Henceforth, it’s highly recommended to use either of the two default policies suggested below.
The following screenshots show the settings of the two default IKEv1 and IKEv2 IPsec policies in CE XDR:
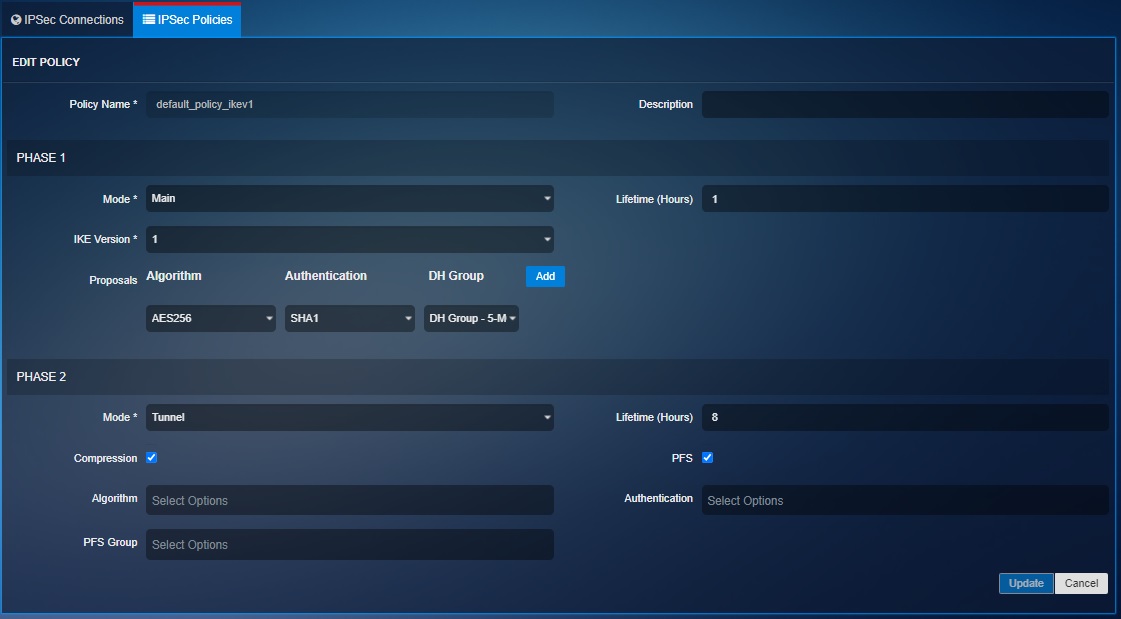
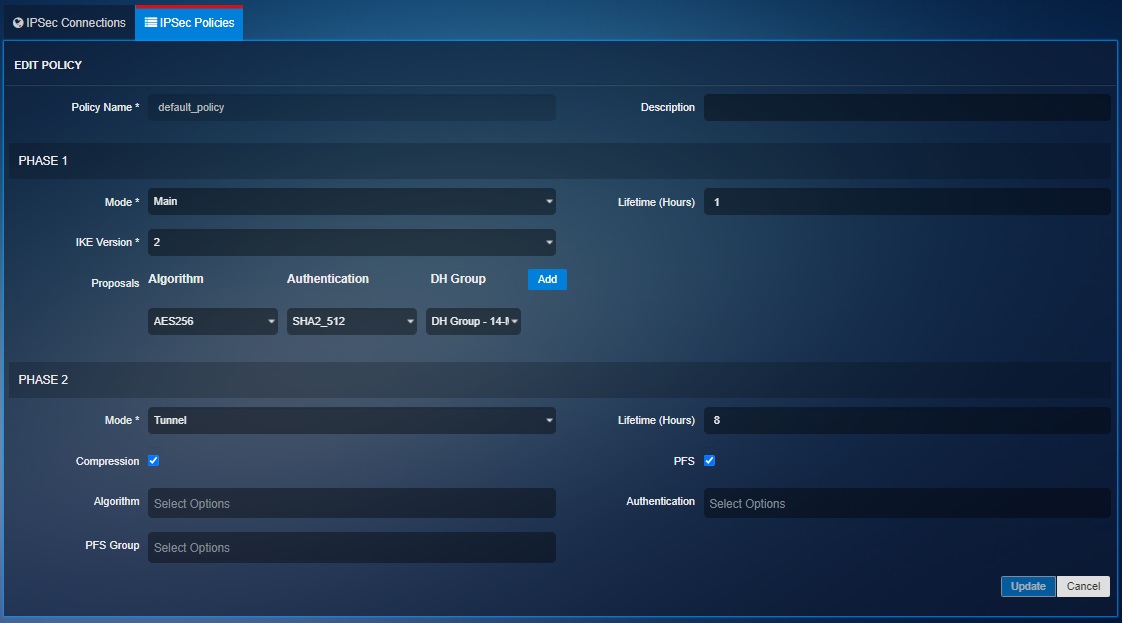
Crystal Eye XDR administrators are advised to replace all pre-shared keys on a regular basis as there are possibilities of it being compromised due weak cryptographic standards.
The following outdated cryptographic algorithms must not be used:
- 3DES
- Diffie-Hellman groups 2, and 5
It must be noted that cryptographic standards change at regular intervals as new vulnerabilities and weaknesses are detected in these algorithms. CE XDR administrators are recommended to be well versed with the latest trends in cryptographic agility. This can be done by staying on top of the latest CNSSP and National Institute of Standards and Technology (NIST) cryptographic recommendations.
Assigning custom IDPS rules to IPsec VPN traffic
IDPS rules aimed to monitor malformed IPsec traffic and inspecting IPsec session negotiations must be deployed in front of the VPN gateway. This can essentially be done with the help of Intrusion Detection and Protection application of the CE XDR.
Enabling Multi-factor Authentication Mechanism for SSL VPN Users
Crystal Eye SSL VPN user profiles must be configured to use multi-factor authentication as a secure authentication mechanism to connect to the Lan networks/servers of the organization. The MFA capability can be activated through SSL VPN server section of the application.
Creating Multiple SSL VPN User Groups & Assigning Advanced Firewall Policies
It is advisable to create different SSL VPN user groups in accordance with the levels of access required for them. The SSL VPN application allows CE XDR administrators to created multiple SSL VPN servers and assign user group/groups to it.
These groups can also be given access to a particular security zone (both default and custom zones) of the CE XDR based on the network topology. The diagram below shows that SSL VPN user 1,2 & 3 have been given to the LAN Zone, Custom Zone and DMZ Zone of the CE XDR Network respectively.
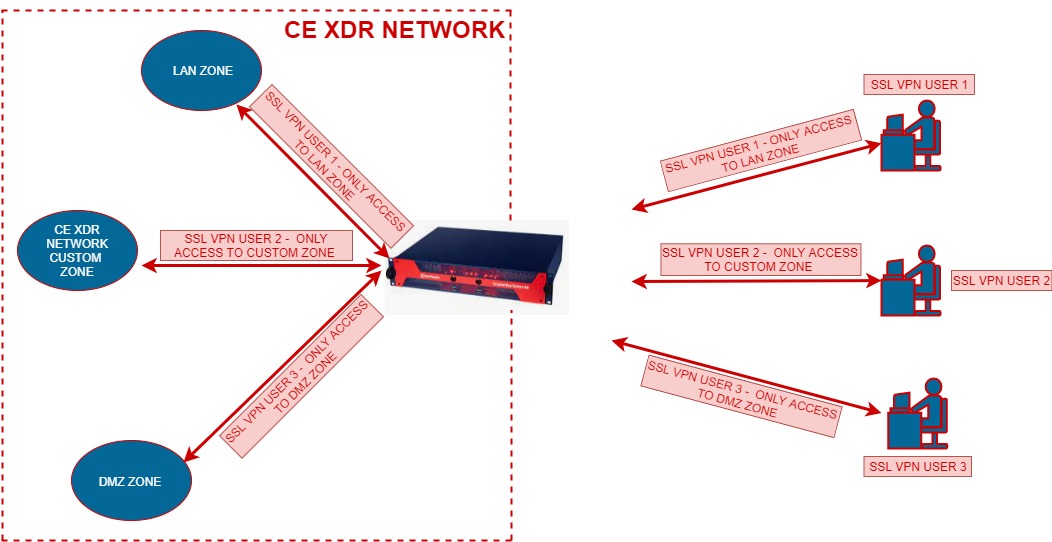
This capability of segregating SSL VPN users to various groups and assigning access to a particular zone also provides the leverage to enforce advanced firewall policies to the SSL VPN users. All the advanced firewall rules assigned to a particular security zone of the CE XDR will also be applicable to the SSL VPN User in that zone.
Remote Support Access
The in-built remote support feature of the CE XDR when enabled allows the technical support engineers of Red Piranha to take over the CE XDR remotely to resolve any challenges faced by the user. This support feature ensures that the CE XDR is reachable behind NAT for remote access.
Implementing DNS Threat Prevention & Blocking Capabilities
The CE XDR has an in-built DNS sink hole functionality that blocks websites deemed malicious by Red Piranha’s update servers connected to the CE XDR.
The diagram below shows:
- How all the DNS requests originating from the endpoints is resolved by the CE XDR.
- CE XDR automatically blocks access to malicious websites.
- It also shows that the CE XDR gets its DNS sinkhole updates from a dedicated DNS sinkhole update server
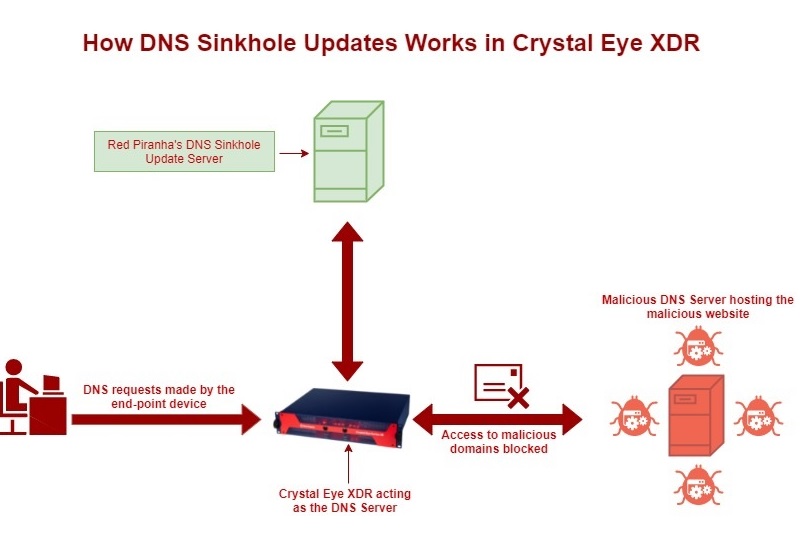
Apart from this, the DNS server application has dedicated section called ‘DNS Banned Domains’ that allows administrators to ban domains on the entire CE XDR network.
Monitor DNS Traffic for other Anomalies
The reports section of the DNS Reports application must be referred to peek into various DNS related indicators such as DNS requests, over time, Top request RRNames, Top response Data, Top DNS Servers, Top DNS Clients, Top Request Types, and Top Response Error Codes.
Avoid Port Forwarding for Remote Access & Use Crystal Eye XDR’s Secure SD-WAN Instead
Port forwarding for remote access is a common practice in many networks and at times is considered much more convenient than setting up a secure VPN. Opening ports for remote access also make it possible for the networks to be vulnerable to unauthenticated attacks where a sequence of specially crafted packets can be sent to gain full control.
The CE XDR offers its SD-WAN platforms that allows a flawless solution such as IPsec VPN for site-to-site connections and SSL VPN for remote access. Stringent policies must be constituted to ensure that CE XDR’s SD-WAN is preferred over port forwarding for remote access.
Advanced Firewall Rules Best Practices
The following recommendations should be practiced and considered as guidelines after a careful assessment of the CE XDR network:
The base advanced firewall rule set should be ‘deny all traffic’ and ‘permit-by-exception’: The CE XDR advanced firewall application can be used to deploy the ‘DENY ALL’ except for the pin holes that are required for various business processes to be executed.
-
Case-by-Case Approach: All communications between the CE XDR network and external networks must be enabled only on case-by-case basis.
-
Risk Assessment of Incoming and Outgoing Network Traffic: A statement of applicability (SOE) must be created with a documented business justification post risk analysis for each permitted incoming and outgoing flow of data. A risk owner for the same must also be assigned.
-
IP and Port specific Permit Rules: If a permit rule is created then it’s recommended for it to be port (TCP/UDP) and IP address specific.
-
Block FTP protocol throughout the CE XDR Network: FTP is used for transferring files between two networks and is well known for its ability to use minimum processing power. The FTP protocol was never designed with security in mind and has a track record of being vulnerable to buffer overflow vulnerabilities. Henceforth, its highly recommended to block this protocol in the CE XDR network. The advanced firewall rule can be used to implement this.
-
Do not allow all traffic from any source on any port to any destination
-
Only allow port 80 (HTTP) and port 443 (HTTPS) in case there is a public facing web server deployed in the CE XDR network.
-
Do not ever allow RDP access from any source to a web server. Always specify the source IP address of the administrator’s computer from where the remote access is required.
-
Do not allow MySQL access from any source to the database server. Many businesses consider allowing SQL traffic originating from any source through the firewall. A traffic rule instead must be created to specify a source IP address to access MySQl server in the CE XDR network.
-
Correct Firewall Rules Order: The firewall rule are generated top to bottom and as a general practice its recommended to have firewalls that are more specific to precede the general firewall rules in the top to bottom order.
-
Firewall Audit: The CE XDR administrator must always ensure that all the advanced firewall app rules must be audit frequently at regular intervals. Such an audit must be conducted to identify unused rules and these rules must be erased from the CE XDR.
-
Customized IDPS must be assigned to firewall rules to ensure that an in-depth security strategy is implemented.
-
Firewall rules logging: As a general practice its recommended to ensure that all the firewall rules are logged. Logging of the firewalls provides the mush needed audit trail of the network activity that can come handy. Such a provision is there in the advanced settings of the advanced firewall application.
-
Group firewall rules: Ensure that the firewall rules are groups WAN to LAN and LAN to WAN to reduce human error and simplify administration of these firewalls. As a rule of thumb, it is advisable to pay more attention to WAN to LAN rules.
NAT (Network Address Translation) Best Practices in the CE XDR
It is recommended to ensure that the NAT rule is deemed necessary based on the specific business requirement that it serves. Based on the necessity of the NAT’ed traffic it must be decided whether the required function can be achieved through another mechanism.
It is seen that NAT is used to allow traffic to host. However, there must be considerable levels of analysis as to where reverse proxy traffic from WAN to DMZ can be used instead.
NAT is considered as an excellent mechanism to ensure that traffic passes through two designated networks. However, it should be considered that NAT rules are configured for some services and not for any services.
Monitoring CPU and Memory Utilization of the CE XDR
A process must be devised to ensure that the CE XDR CPU and memory utilization is monitored at regular intervals by the CE XDR administrator from the System Dashboard. The system resource report can also be referred to for further analysis of the system load, memory, swap memory, processes, and uptime.
Monitor Credit Card and SSN Related Data Movement
It is recommended to activate credit card & SSN monitoring feature of the DLP application. The CE XDR administrator can adjust the alerting mechanism as per business requirements. This also means that the alert would be triggered if a minimum of 3 credit card numbers and 5 social security numbers are sent to an external network from the CE XDR network.
Credit card numbers and social security numbers come under the category of Personally Identifiable Information (PII) which is highly sensitive and protected by laws such as GDPR etc. Henceforth, its highly important to activate the credit card/SSN monitoring feature to comply with laws pertaining to various regions of the word.
Crystal Eye XDR Enhanced WAN Hardening
In some cases, it may be a site requirement to limit external access to the Crystal Eye WAN interface.
Some of the simpler competing firewalls that lack IDPS, Zone control etc. do not prevent flow between WAN and LAN interfaces and as a result it is common to implement a policy to block all inbound WAN traffic and only allow for inbound services on an as-needed basis. Crystal Eye by default does not allow inbound traffic to pass through directly from WAN to LAN. This teamed with the managed IDPS, threat intelligence feeds, SIEM monitoring, Content Filtering, Automated Actionable Intelligence, Direct SIEM and SOC integration out of the box not only raises the bar for attackers, it makes it possible to detect a breach within minutes as opposed to the usual dwell time of months before attacks become apparent.
DISABLING THESE PORTS WILL IMPACT SUPPORT SERVICES AND THE COMMUNICATION OF DEVICE TELEMETRY TO THE RED PIRANHA THREAT INTELLIGENCE PLATFORM AND IS NOT RECOMMENDED FOR MOST DEPLOYMENTS.
In cases where it is a policy requirement, it is possible to disable access to these services with the following steps.
SSH is a support channel that is used exclusively by authorised Red Piranha support engineers and access is limited to specific IP addresses. This service can be disabled using either of the 2 following methods.
Method 1 - Navigate to https://crystaleye.lan:81/app/ssh_server and click the "Stop" button. This will disable the SSH service until the Crystal Eye is restarted or the service is manually started.
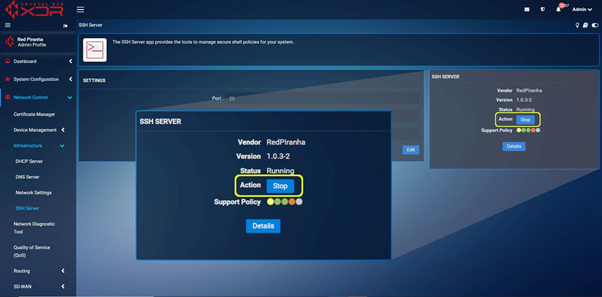
Method 2
Step 1 : Navigate to https://crystaleye.lan:81/app/ssh_server and edit the port used by the SSH service to an unused port (like telnet – 23).
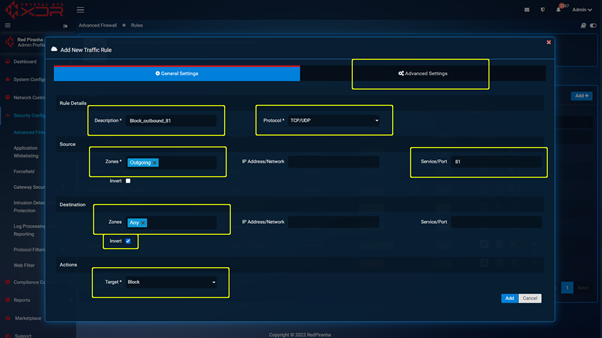
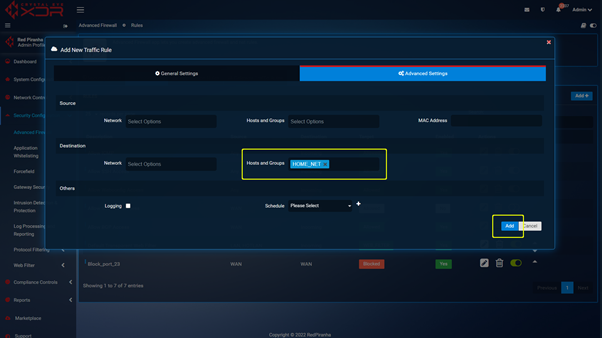
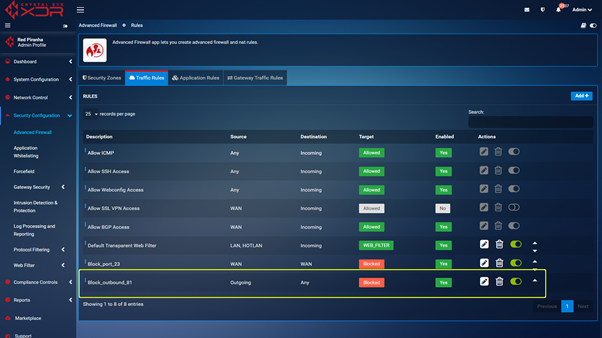
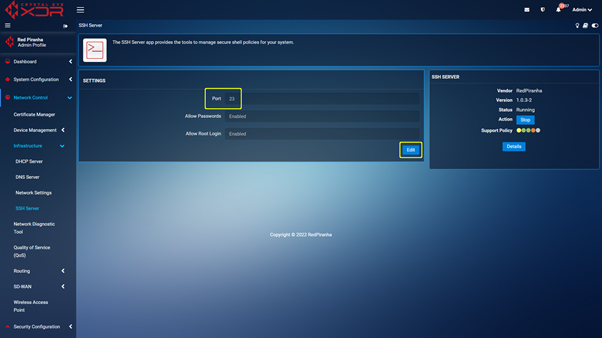 Step 2 : With the port changed you can navigate to https://crystaleye.lan:81/app/firewall and add a new Traffic Rule configured to block WAN access to the port defined in the previous step.
Step 2 : With the port changed you can navigate to https://crystaleye.lan:81/app/firewall and add a new Traffic Rule configured to block WAN access to the port defined in the previous step.
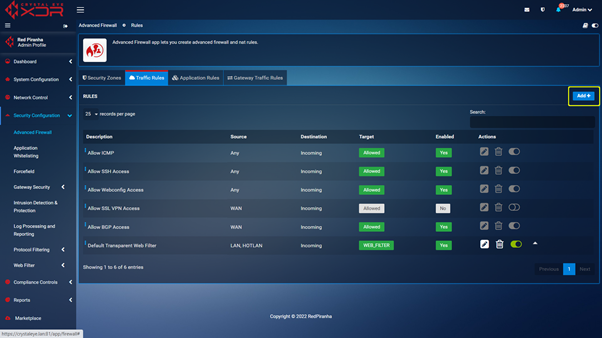
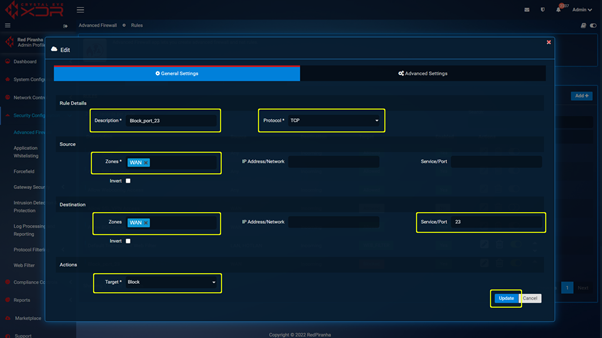
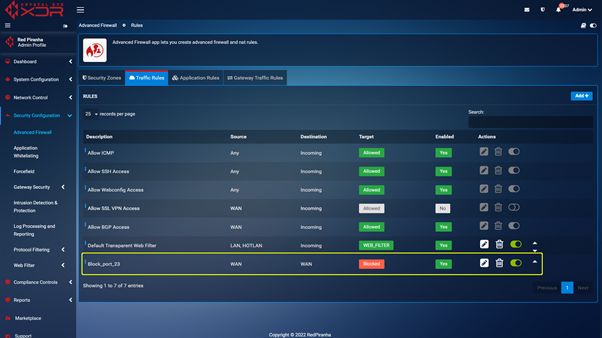
Web GUI is the web based interface used by Red Piranha support, MSP/MSSP staff and authorised customer staff to manage the Crystal Eye XDR appliance. Disabling Web GUI access will result in the Crystal Eye XDR management interface being no longer available from locations not on the LAN side of the XDR appliance. This can only be reversed via the Web Interface on an endpoint connected to an interface serving the LAN zone.
As inbound WAN requests cannot be disabled, blocking outbound requests on port 81 will not allow WAN side access requests to complete.
Navigate to https://crystaleye.lan:81/app/firewall and add a new Traffic Rule to block outbound connections on port 81 using the following settings.