Risk Auditing
The Risk Auditing app is used in conjunction with Red Piranha’s eCISO service. It contains easy-to-answer yes/no questions based on the Centre for Internet Security (CIS) best practices, and Red Piranha Limited’s set guidelines specifically tailored for SMEs to validate and determine your company’s level of compliance defined within this guideline. This guideline is a recommended set of actions for cyber defence that provide specific and actionable ways to stop today’s most pervasive and dangerous attacks.
The assessment and auditing features of the app is designed to enable an administrator to answer a risk management related questionnaire and make judgments accordingly. The app supports risk auditing and assessment of multiple assets owned by a particular organization.
Upon submission, the completed questionnaire is sent to Red Piranha’s Risk Server which creates a report that will be incorporated into the Cybersecurity Review performed as part of the eCISO process.
The report can also be viewed in the Orchestrate Dashboard.
This process of internal risk auditing finally defines the risk posture of the company/business.
The Risk Auditing application is installed by default and can be accessed from the left-hand navigation panel.
Left-hand Navigation Panel > Compliance Controls > Risk Auditing
The risk control process starts with analysing and assessing the risks associated with various types of assets. Crystal Eye’s Risk Auditing app has excellent features that enable CE administrators to perform a comprehensive internal risk assessment. The questions asked in the critical security controls section of the risk auditing app has been formulated to identify various risks involved with a particular asset. If the answer is a “Yes” then that parameter is not considered as a risk. However, if the answer is “No” then that risk parameter turns into a potential risk and gets registered under the Pending Risks section.
Once the risks are identified and are transferred to the pending risks section the CE administrator can easily view/edit the following sub-parameters related to the newly created risk.
Submission Date – The date at which the risk was identified and created in the Risk Auditing app.
Subject – Brief description providing details of the risk.
Risk Score – Rating the risk on a scale of 1 to 10.
Owner – The owner of the asset for which the risk was created.
Asset Name – The name of the asset for which the risk assessment is done.
Additional Notes – Additional information regarding the identified risk.
After the edits are confirmed, the risk details can be sent to Red Piranha’s risk assessment team for further analysis and mitigation.
How to Assess Risks Associated with an Asset Belonging to a Company/Business/Organization?
Step 1: In the Risk Auditing application page, click the Select Critical Security Controls button.
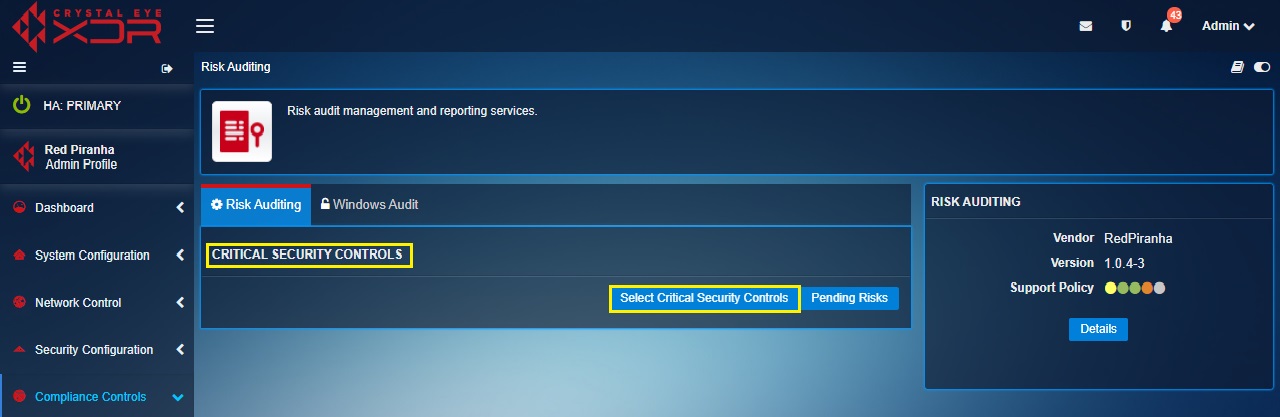
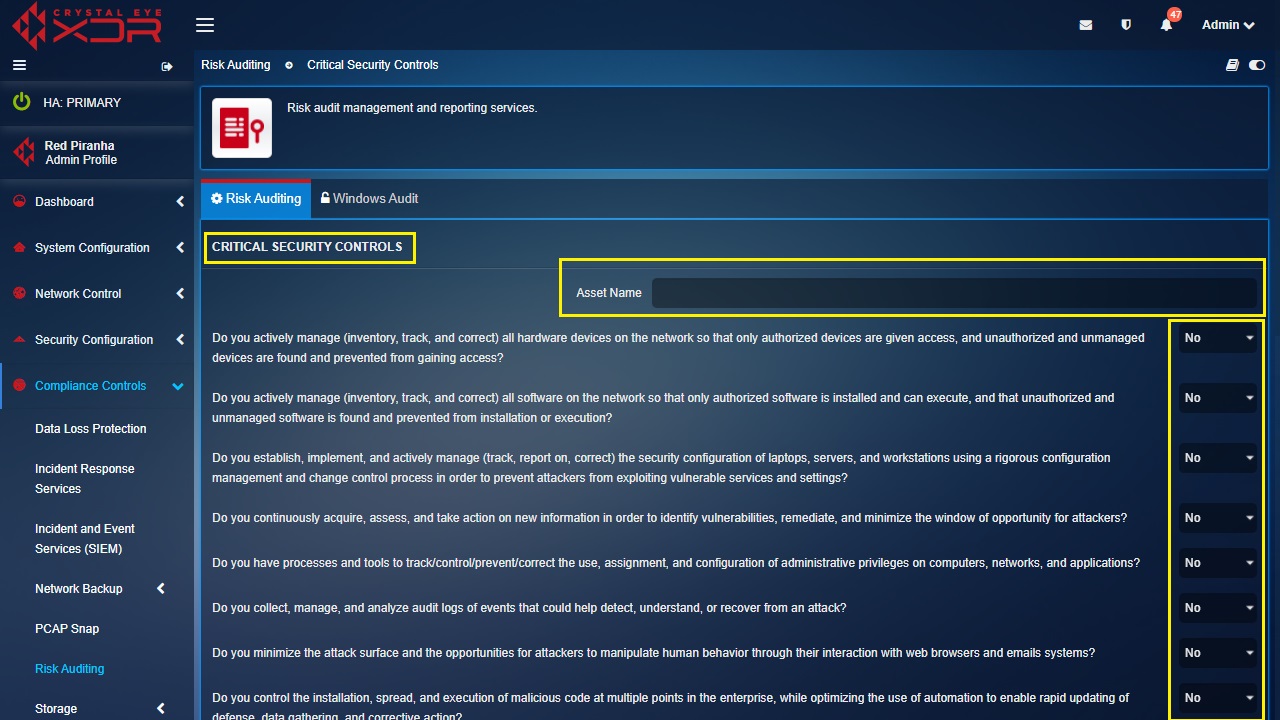
Step 2: You will now see the Critical Security Controls questionnaire page. Enter the Asset Name for which the risk needs to be assessed, then answer each question by selecting Yes or No and click the Submit button. A risk will be created for each “No” answer under the Pending Risks section.
(the Asset Name is the Crystal Eye Account name linked to the eCISO service or can be left blank)
After clicking Submit in Step 2, the Pending Risks screen containing a list of applicable risks, will be displayed. A risk will be created for each “No” answer in the Step 2 questionnaire.
Step 3: Assign a responsible Owner to each Pending Risk and with the help of the eCISO select a Risk Score rating.
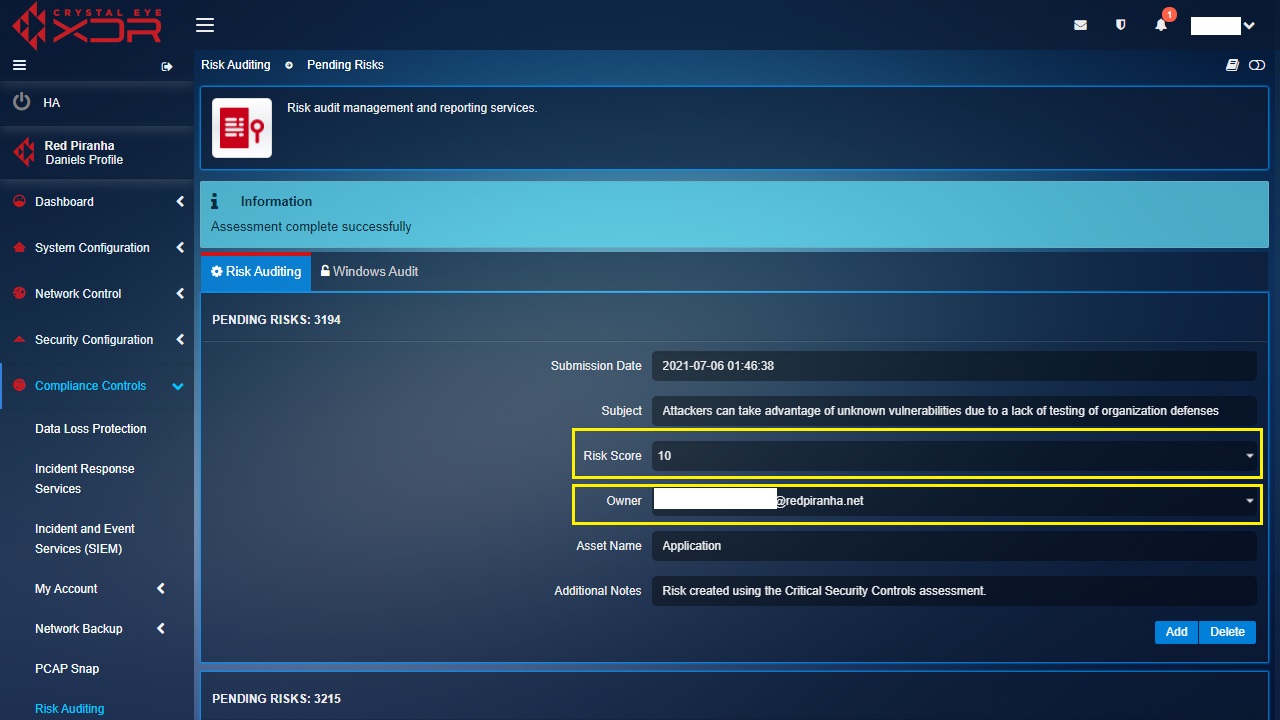
Step 4: Click the Add button on each risk to push the risk to the Red Piranha Compliance team for analysis. A risk can also be deleted if it is determined to be not applicable to your organisation. It is recommended that you check with your eCISO Risk Advisor for advice.
The Crystal Eye Attack Surface Reduction (CEASR) application ensures devices on your network conform to security policies based on standard security frameworks such as the Australian Signals Directorate's Information Security Manual (ISM) and the Essential Eight guidelines. It also allows CE XDR administrators to apply operating system policies across a range of devices and provide ongoing device monitoring to keep track of your compliance baseline in real-time.Know more about CEASR Application