ZTNA and Crystal Eye
With increased pace of digitization triggered by the Covid-19 Pandemic, the network security requirements of organizations have undergone a drastic change. Network security solutions are now being more focused on challenges faced by cloud or remote users. The shift of businesses to cloud and work from home models including BYOD policies comes coupled with increased information security risks. There are high chances of compromise of confidentiality, integrity and availability of data.
In a survey conducted by HP it was found out that:
-
70% of office workers surveyed admit to using their work devices for personal tasks
-
69% are using personal laptops or printers for work activities.
-
30% of remote workers surveyed have let someone else use their work device
Many of the leading companies have announced their decision to continue with the work from home or hybrid working model which means that these issues are here to stay.
Zero Trust Network security model is a departure from the traditional perimeter security model. As the name suggests, it works on the principle of reposing zero or no prior trust in the subject (entity/person requesting access to resources or trying to enter the network) but continuously authenticating and granting access on a least privilege basis. Instead of protecting only the perimeters, the security policies should be customized with respect to each protect surface, thus extending protection to internal network as well. It is irrelevant whether the subject is internal or external. As per NIST SP 800-207, it is based on principle “Never trust, always verify”.
ZTNA is not a single network security solution but an amalgamation of multiple applications and capabilities which in totality helps in achieving Zero Trust Network Security. Crystal Eye XDR comes with a unique blend of these capabilities which help in accomplishing ZTNA.
-
Authentication and Authorization: ZTNA is based on the principle of continuous authentication and authorization of subjects. Multi-factor authentication provided by Crystal Eye ensures that only authorized access is made to the network resources.
-
Least privilege principle: The user access management is designed in such a way that privilege is granted only on need-to-know or need-to-do basis.
-
Data Protection: Protecting data which is indeed the new oil is what our Data loss prevention application does. With a secured gateway feature, Crystal Eye prevents any unauthorized movement of data through the network.
-
Multi-tenancy and Network Segmentation: Hosts and groups/zones/network segmentation enables us to prevent lateral movement and minimizes loss in case of security breach as the attack surface gets reduced.
Some challenges which the organizations usually face while implementing a Zero Trust strategy are:
-
Complexity without unified approach
-
Unifying Identity and Access Management
-
Managing staff on boarding and off boarding
-
Establishing User Trust
-
Establishing Device Trust
-
Mapping transaction flows in well-established systems
Red Piranha through its unique approach towards ZTNA manages to overcome the above-mentioned difficulties. By deploying Crystal Eye, the user enjoys:
-
Reduced complexity – one vendor
-
Synchronised identity and access management – user verification
-
Unified asset management – device verification
-
Application of security controls and monitoring as well as access control
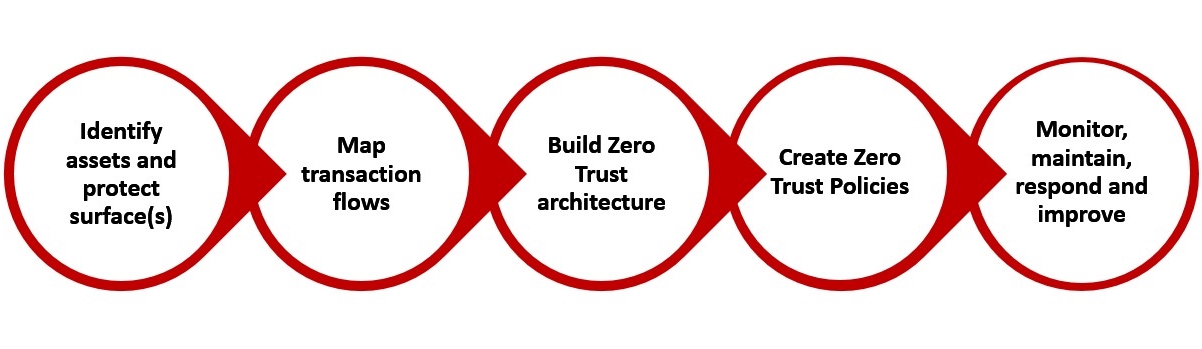
-
In order to achieve ZTNA, the first and the foremost step is to identify the assets or resources which you are trying to protect. There is no threat without an asset thus identifying the protect surfaces and their relative priority levels is very important. This can easily be done by asking some simple questions.
- What are you trying to protect? What are your crown jewels?
- Where are they located?
- Who can have access to it?
- When should the access be given? (Time duration)
-
Once the assets have been identified, the next step is to map the flow of transactions in the network. Identify the communication paths through which packets travel to and from the asset.
-
Next step is to deploy the Zero Trust solution at such a place such that all the traffic that flows to the protect surface has to pass through the ZTNA solution for the purpose of authentication and authorization.
-
We need to create a set of well-drafted and clear policies and access rules on the basis of which the ZTNA would function.
-
Lastly, we need to monitor the compliance with the policies and update the policies where there is scope for improvement.
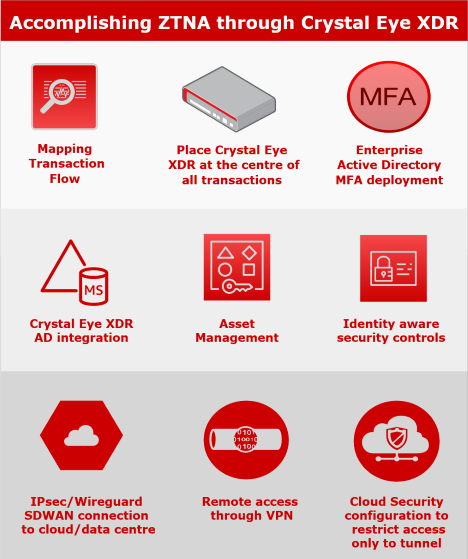
-
Hosts and Groups: They are the segmentation building blocks in Crystal Eye. It enables us to combine multiple network entities into a single group. The app also allows users to create firewall objects to represent a variety of items in a firewall rule. It can be used across applications in Crystal Eye using UCMI architecture. If a modification is made in the hosts and groups app, the effect can be seen in all the applications across the Crystal Eye appliance.
-
Advanced Firewall Zones: Zones help us to virtually divide the network into separate sub-networks. Each sub-networks can have different policies and are the building blocks of multi-tenancy in Crystal Eye. Once we have identified zones, we can apply different policies to a particular zone. It can act as a separate network within Crystal Eye. Crystal Eye XDR has 4 default security zones namely, LAN Zone, HotLAN Zone, WAN Zone and DMZ Zone.
Crystal Eye XDR’s Advanced Firewall application has enhanced capabilities to govern, and control inter zone traffic. The traffic rules feature is designed to determine access rights and allow or reject traffic between network object /hosts. It is through these rules that traffic can be controlled by its Source, Destination, Zone, and Service. In addition, the Crystal Eye XDR administrator can assign various firewall policy actions to the traffic such as:
- Allow
- Reject
- Block
- IDPS
- Web Filter (Authentication based & IP/MAC based)
-
Multiple SSL VPN servers with MFA: It secures Inbound and Untrusted Internal Network Perimeter Controls access to enterprise network from the remote client. The SSL VPN application of the Crystal Eye XDR is used to create Remote-access VPN connections in full tunnel mode and split-tunnel mode.
• Create different zones for different access levels
• Use Multi-Factor Authentication
• Advertise only selective subnets
• Control access using Traffic Rules
-
Secure Web Gateway: Secures the outbound network perimeter. This includes web proxy, content filter and antivirus applications. We can create different web filter policies in Crystal Eye using advanced firewall for different zones. This enables Multi-tenancy while scanning the outbound traffic.
• Different Web Filter Profiles for different zones
• Filtering and Block list controlled by Content Filter
• SSL inspection needed to filter SSL transactions
• Authentication should be enabled to authorise users (Crystal Eye/Active Directory)
-
IDPS profiles : It helps secure the inbound and outbound perimeter. We can run different profiles in different zones in Crystal Eye. These profiles use security rule sets that are curated by SOC teams and downloaded from the update server. Alerts produced by IDPS Engine can be escalated to CESOC and enables fast incident response.
• Different profiles for different network segments • Detection profiles
• Inline Profiles
• Security Rulesets (Curated list of around 45k+ rules)
• Alert escalations and tuning
-
Advanced Firewall Traffic rules: It enables access control between zones. We can apply different web filter policies using traffic rules or different inland IDPS profiles to different zones. It helps secure all the Network Perimeters and enables true multi-tenancy using Crystal Eye.
• Control Access between zones
• Use Hosts and Groups to group different devices and sites together
• Applies the Web Gateway and Filter policies
• Applies the inline IDPS profiles to different network segments