SSL VPN
Crystal Eye’s SSL VPN application allows administrators to connect two CE appliances and is also used to configure Remote Access VPN. By connecting two CE boxes the administrator would essentially be able to establish a Site-to-Site tunnel between them.
Using the SSL VPN application, the administrator can create Remote-access VPN connection. It is a highly secure functionality which essentially allows users to connect to a remote network with the help of secured SSL based connections. Crystal Eye provides cutting edge technology ensuring smooth connectivity over a VPN network. The TLS security certificate that is deployed using the Crystal Eye interface ensures an encrypted connection making it possible for multiple users to connect to a central site.
Left-hand Navigation Panel > Network Control > SD-WAN > SSL VPN  |
|---|
The Global Settings of the SSL VPN application must be configured before initiating the basic and advanced functionalities. The Global Settings include Configuring SSL Certificate and then allowing connections from external networks which essentially disable’s the firewall feature that blocks external connections.
The Configuration of SSL Certificate generates a security certificate which plays a crucial role in providing an extra layer of security by providing an encrypted connection.
Note: The Global settings include configuring an SSL certificate. This must be done before setting up a Remote-access VPN or a SSL Site-to-Site VPN
How to Configure Global Settings of the SSL VPN Application?
Step 1: In the SSL VPN Application page, click Configure Security Certificates button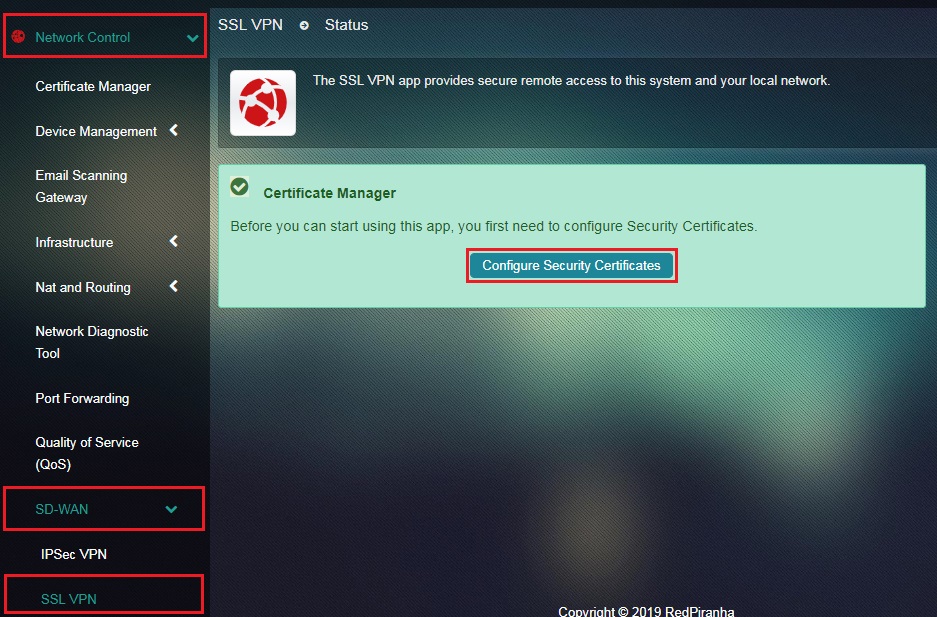 .
.
Note: This step initiates the process of generating an SSL certificate which plays a crucial role in providing an extra layer of security by enabling an encrypted connection.
Step 2: You will now see the Certificate Authority page. Enter the Internet Hostname, Organization Name, Unit Name, City, State, and Country in the respective text boxes and click Create Certificate. 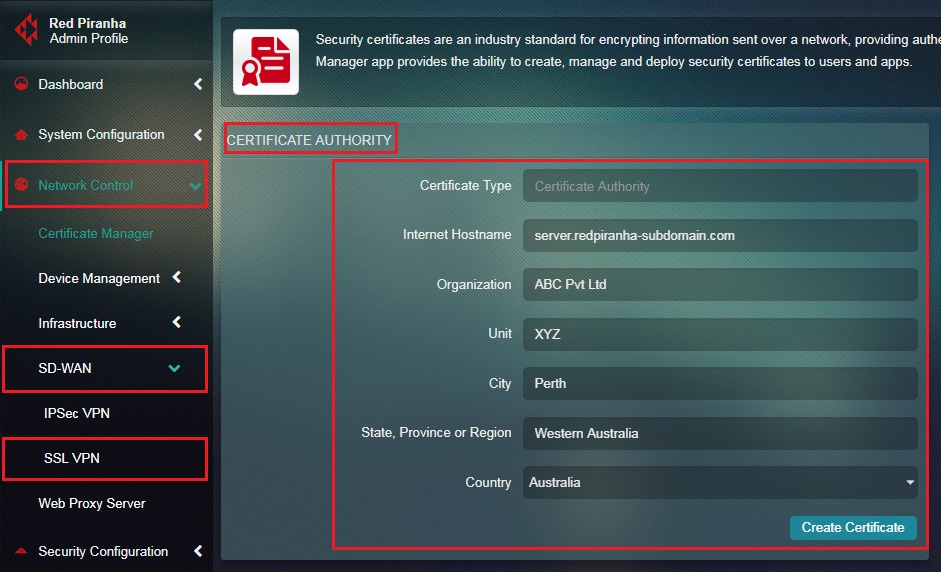
Note: If you are running system as a standalone server on your local network, your internet hostname (e.g. myserver.example.com) may differ from the internal hostname used by Crystal Eye.
Step 3: Click the Continue button to move on with the new SSL Certificates.
Note: After you click the continue button, the web interface will automatically restart after generating the new SSL certificate. You will then be redirected to the Certificate Manager application page (as shown in the screenshot below).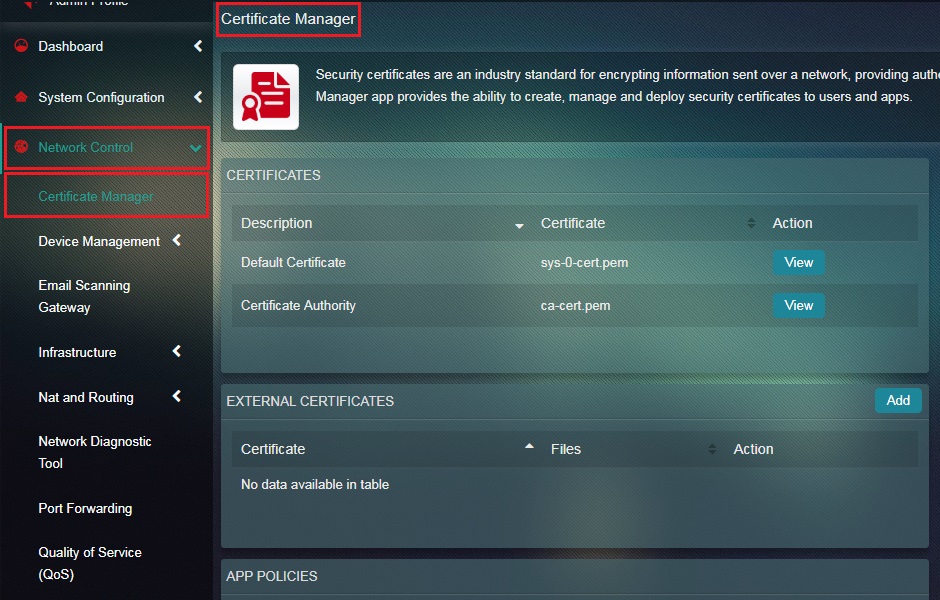
Step 4: Browse back to the SSL VPN application page. Click SSL VPN in the left-hand navigation menu under the SD-WAN Category.
Step 5: You will now be directed to the SSL VPN application page. Click the Allow Connections button in the pink warning box.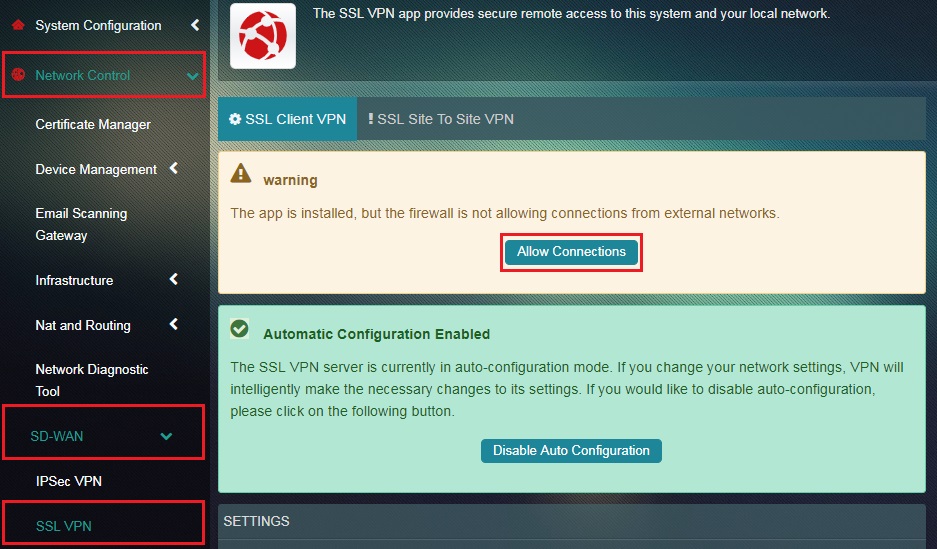
Note: You would also notice a message in a green box which says, “The SSL VPN server is currently in auto-configuration mode. If you change your network settings, VPN will intelligently make the necessary changes to its settings. If you would like to disable auto-configuration, please click on the following button”. (We recommend not disabling auto configuration).
Crystal Eye’s Remote-access VPN is an essential user-centric functionality which allows users to connect with a remote network with the help of secured connections. Crystal Eye provides cutting edge technology ensuring smooth connectivity over a VPN network. The deployed SSL certificates ensure a secure connection making it possible for multiple users to connect to a central site.
Configuring a Remote-access VPN Connection includes generating a self-signed SSL Certificate and deploying it. The SSL certificate when deployed provides an extra layer of security by providing an encrypted connection. The process of generating self-signed SSL certificates are discussed in detail in the Global settings section.
The configuration process also includes entering an A record in your DNS that points to your external IP. Doing so means that in the event of your IP address changing, you only need to make one change to allow your users to continue connecting, compared to having to edit each configuration file manually. You may need to refer to your DNS provider for instructions on how to do this. Please note that you can easily find your connection’s external IP with a quick Google search for “What is my IP”.
The Remote-access VPN users can be added using the user app. The users can then login to the Remote-access VPN network through OpenVPN after importing OpenVPN Configuration File.
How to Set-up a SSL Certificate Based Remote-access VPN Application?
Note: Please make sure that the Global Settings are configured before initiating the SSL VPN configuration process.
Step 1: Ensure that you have a valid external hostname as the internet hostname of your device. We recommend you use the default internet hostname i.e server.redpiranha-subdomain.com.
Note: If you want to use custom internet hostname then you would have to add an A record to your DNS that points to your external IP, to make management more manageable in the future. Doing so means that in the event of your IP address changing, you only need to make one change to allow your users to continue connecting, compared to having to edit each configuration file manually. Due to the number of DNS providers, you may need to refer to your DNS provider for instructions on how to do this. Please note that you can easily find your connection’s external IP with a quick Google search for “What is my IP”. You can also use the external IP of the CE as the internet hostname. refer to step 2 incase you want to change the internet hostname. If you dont want to alter the internet hostnaame then skip to step 5..
Step 2: Once the A Record has been added, navigate to the IP Settings application (Left-hand Navigation Panel > Network Controls > Infrastructure > IP Settings)
Step 3: You will now see the IP Settings app page. Click Edit in the Settings section.
Step 4: You will now see the editable version of the Settings section. Replace the contents of the Internet Hostname field with your new A record and click Update button. Please note, in this example we will use vpn-example.redpiranha.net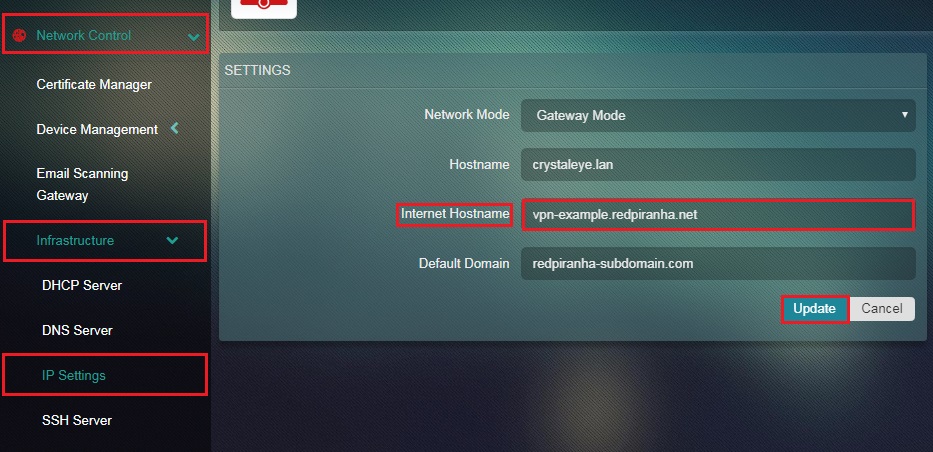
The following set of steps from Step 5 to Step 17 are done to add new SSL VPN users:
Step 5: Navigate to the Users application in the left-hand navigation panel. Navigate to Users app: Left-hand Navigation Panel > System Configuration > Account Roles > Users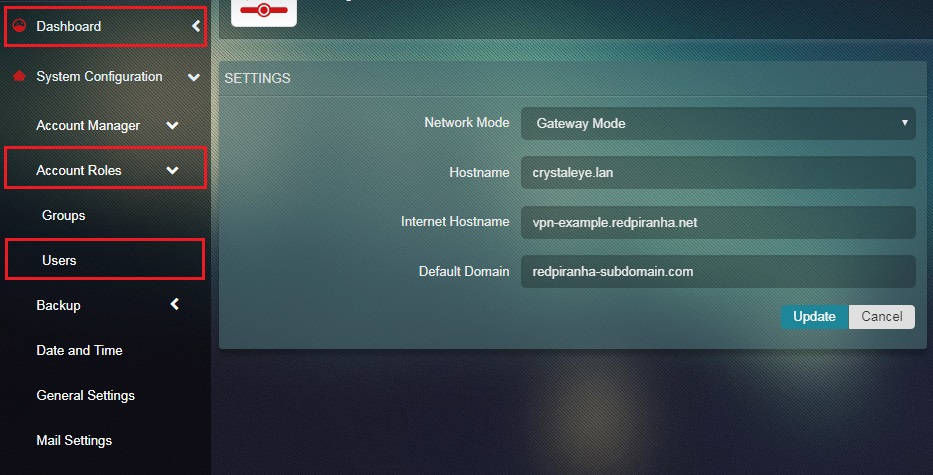
Step 6: You will now see the Users application page. To add a new user, click the Add button under the User Manager section.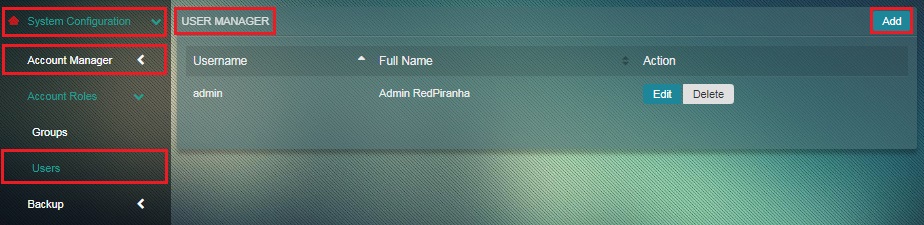
Step 7: You will now see the User page. Enter the Username, First Name, Last Name under the Name section.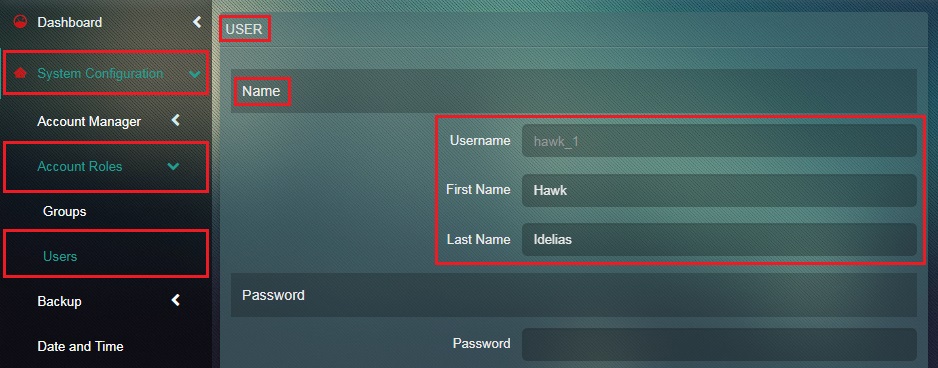
Step 8: Now, enter the desired password and re-enter it in the field below.
Note: Red Piranha recommends using strong passwords of at least 20 characters in length made up of numbers (123) letters of mixed case (ABCabc) and symbols ($%^&) in your passwords. We also recommend instructing your users in proper password storage, to prevent loss or leaking of credentials)
Step 9: In the App Policies section, use the Enable/Disable dropdown to enable or disable OpenVPN User, Security Certificate User, and Web Proxy User.
Note: Users created will have OpenVPN, Security Certificate and Web Proxy enabled by default.
Step 10: In the Groups section, select the desired Group tickbox to select the group to which the user is to be added and click the Add button.
Note: Do not select the Admin Group. Instead, create a new group and assign the user to the new group. Click here to know how to create a new group. After filling in the user form and saving it, you will be presented with the user list again, with your newly created user.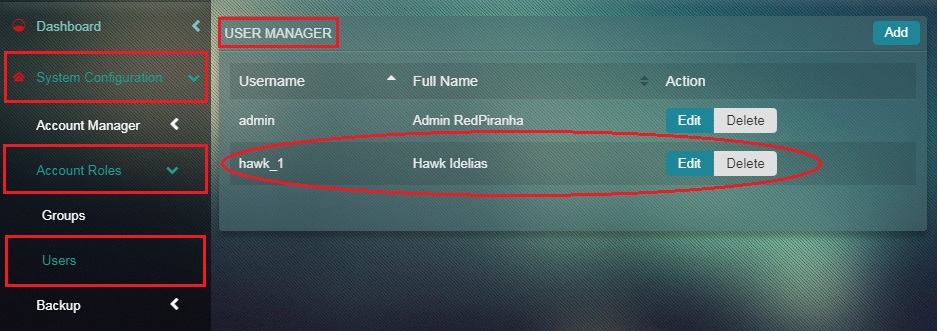
Step 11: Log in to CE as the newly created user using the new password.
Note: In this case the new username is test_user1
Step 12: Navigate to Compliance Controls > My Accounts > User Certificates
Step 13: You will now see the User Certificates app page. In the Settings section, enter the password of the newly created user under the Settings sections and click Create Certificates button.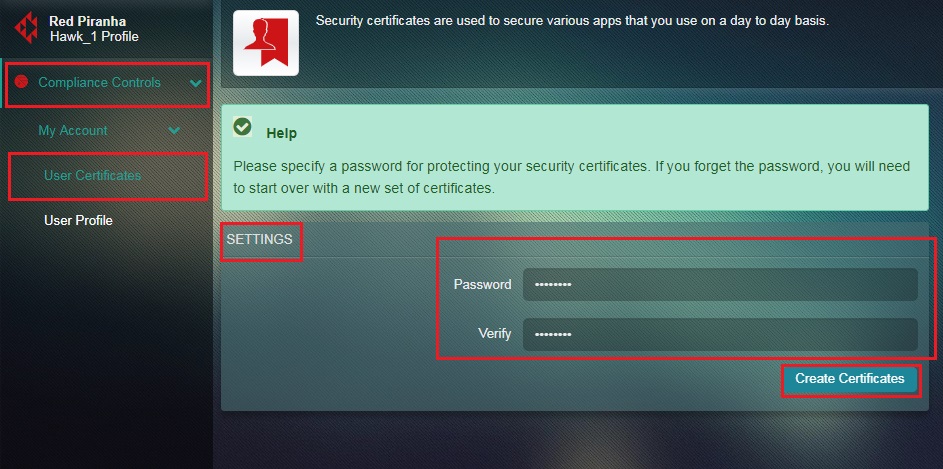
Step 14: You will now see the interface to download the configuration for the OpenVPN client. Under the SSL VPN section select the Operating System for which the OpenVPN Configuration File is required from the dropdown and click the Download button.
Note: User can download OpenVPN configuration file for Windows, Linux and MacOS. Each configuration contains each user’s unique certificates. You cannot reuse a configuration file for every user.
The next set of steps would essentially help in configuring OpenVPN
Step 15: Download and install OpenVPN from https://openvpn.net/community-downloads/
Step 16: Start the OpenVPN GUI As Administrator from the desktop / start menu icon, then right click the icon in the task bar icon and click on Import File. 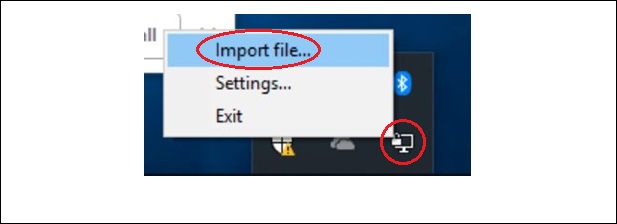
Step 17: Browse to the .ovpn file (OpenVPN Configuration File) and open it. After it is imported, right click on the OpenVPN icon again, and click Connect.
Enter the user’s credentials to get access to the SSL VPN network. The user will be able to access the internet and the gain access to the LAN network as well.
Note: OpenVPN will NOT function properly if not run as administrator.
The remote access VPN settings section of SSL VPN application has explicit configuration settings that allows Crystal Eye administrators to assign static IP addresses to SSL certificate based remote access VPN users.
In default configurations of the Crystal Eye, the SSL-certificate based remote access VPN operates in Auto Configuration mode. The IP address gets assigned dynamically to the remote access SSL VPN users in this mode.
However, CE administrators can also assign static IP addresses for remote access SSL VPN users after disabling auto configuration mode. In addition to this, the range of the static IP address can also be assigned.
How to assign a static IP for remote access SSL VPN users?
Note: The below mentioned steps must be executed after completing all the steps discussed in the Global Settings section.
Step 1: In the SSL Client VPN application page, click the Disable Auto Configuration button in the pop up message.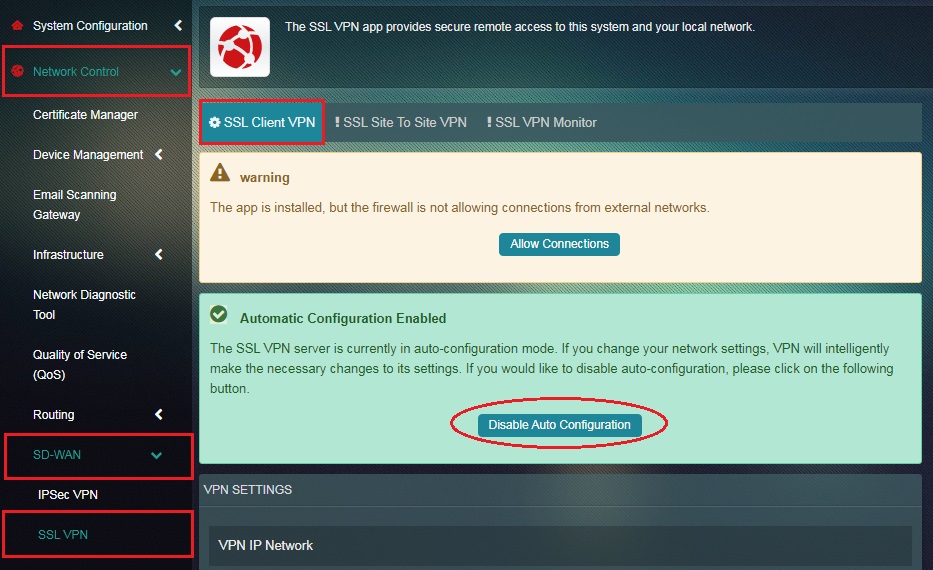
Step 2: You will now be directed to the VPN Settings page (editable version). Enter the IP range that you opt for in the TCP Server and UDP Server textbox under the VPN IP Network.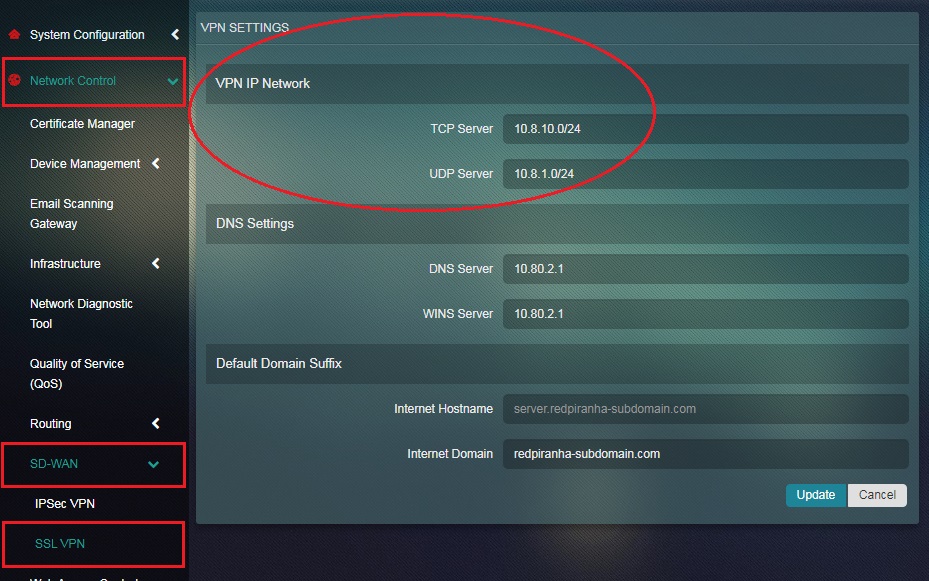
Note: The default IP range assigned for remote access SSL VPN users is TCP Server – 10.8.10.0/24 & UDP Server – 10.8.1.0/24.
Step 3: In the SSL VPN page, click the Assign Static IP button in the User Management section.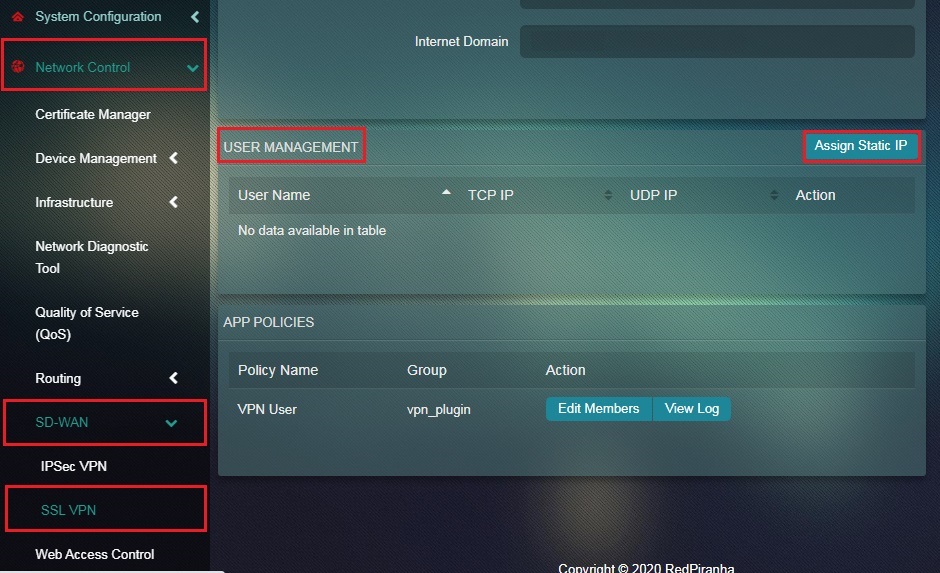
Step 4: You will now be directed to the Add Static IP to User page. Select the Remote access SSL VPN username, assign the TCP/UDP IP address and click the Submit button.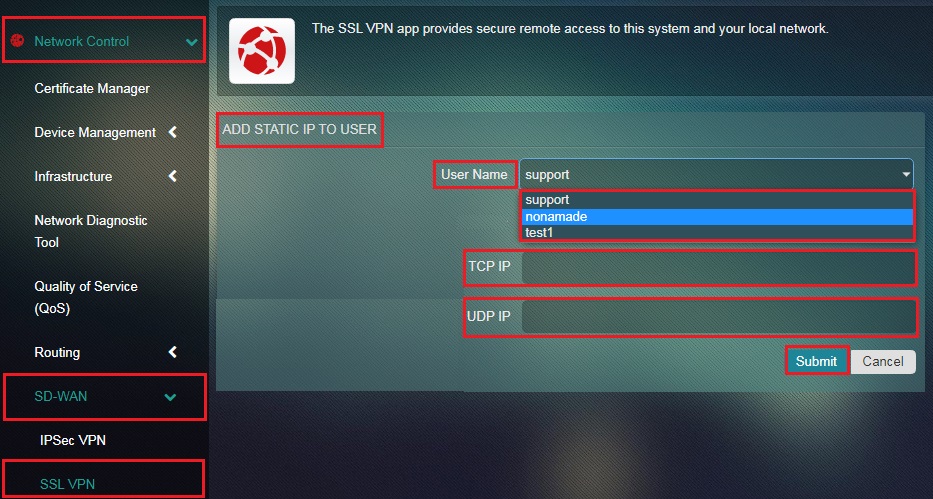
Step 5: The static IP address will now be visible in the User Management section.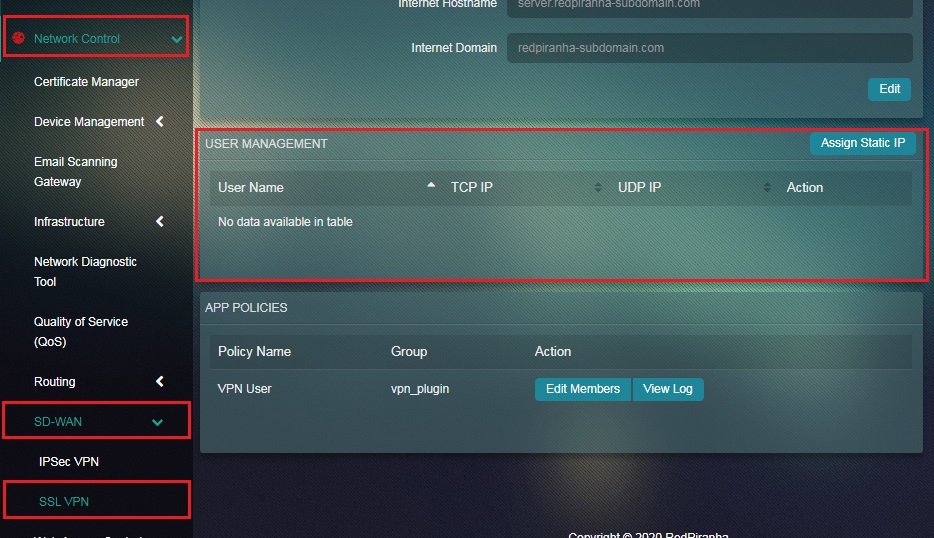
Crystal Eye’s remote access SSL VPN users can be monitored on real time basis and an array of vital information regarding the user can be known. 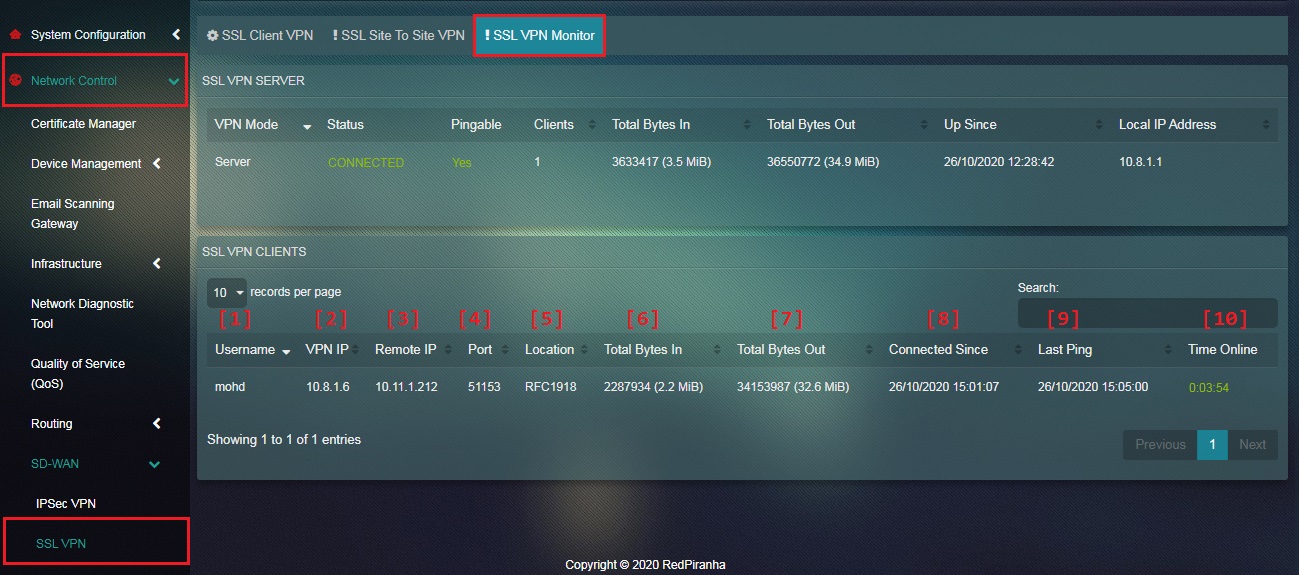
As shown in the screenshot above, the SSL VPN Clients table will show:
- VPN username
- VPN IP
- Remote IP
- Port used by VPN user
- GEO location of the VPN user
- Incoming traffic (Bytes) from the VPN user
- Outgoing traffic (Bytes) from the VPN user
- Time since the VPN user is connected
- Last ping (date and time) by the VPN user
- Overall time the VPN user has been online
As highlighted in the screenshot below, the SSL VPN monitoring dashboard also shares vital VPN server related information such as: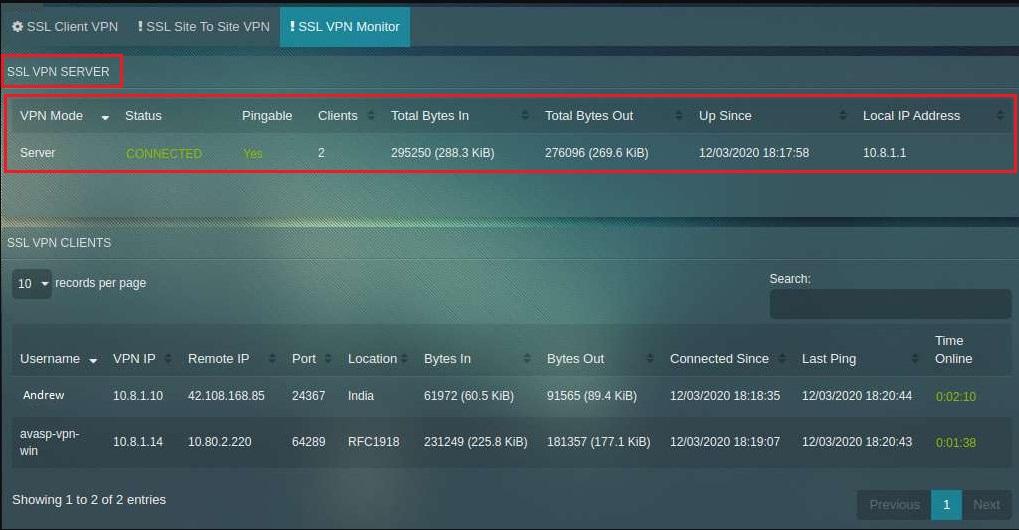
- VPN Mode
- Connection Status
- Server Pingable Status (Yes/No)
- Clients connected to the server
- Total Bytes received and transferred (in KiB)
- The date and time since the server was up
- Local IP address of the server
Establishing SSL Certificate based Site-to-Site VPN involves connecting two sites each having a Crystal Eye appliance. While setting-up a SSL Site-to-Site VPN the Crystal Eye appliance in which the configuration settings are entered is referred to as the Headquarter or Local CE and the Crystal Eye appliance on the other site is referred to as Branch or Remote CE.
The entire process of configuring a SSL Certificate Based Site-to-Site VPN involves configuring both the Crystal Eye appliances located at both sites. The connection process is completed after the administrator uploads the Key and Configuration File at the branch which is originally attained from the headquarters.
For the sample configuration we will use two Crystal Eye appliances to stimulate a SSL Site-to-Site VPN, with the following configurations:
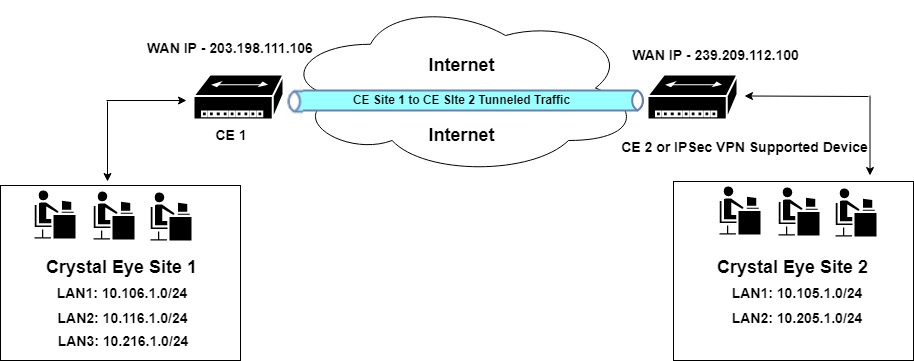
How to Configure a SSL Certificate Based Site-to-Site VPN?
Phase I Configuration - The first phase mainly deals with configuring the Headquarter (Local CE)
Step 1: First, navigate to the SSL VPN application page. In the left-hand navigation menu, click SSL VPN under the SD-WAN category.
Step 2: You will now see the SSL VPN app page. Click Configure Security Certificates button.
Note: This step initiates the process of generating a SSL security certificate which plays a crucial role in providing an extra layer of security by providing an encrypted connection
Step 3: You will now see the Certificate Authority page. Enter the Internet Hostname, Organization Name, Unit Name, City, State, and Country in the respective text boxes and click Create Certificate. 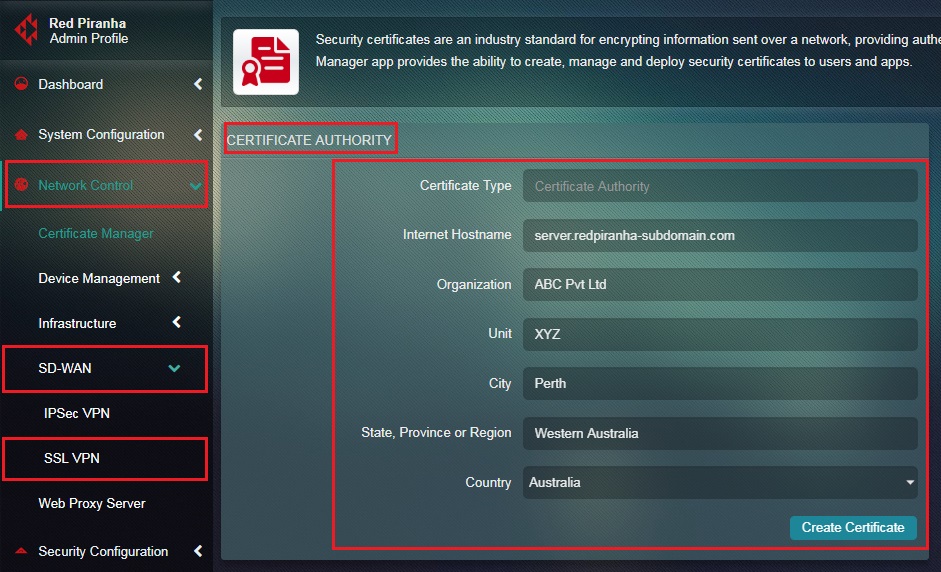
Note: If you are running system as a standalone server on your local network, your internet hostname (e.g. myserver.example.com) may differ from the internal hostname used by Crystal Eye e.g. myserver.lan
Step 4: Click the Continue button to move on with the new SSL security certificates.
Note: After you click the continue button, the web interface will automatically restart after generating the new SSL certificate. You will then be redirected to the Certificate Manager application page (as shown in the screenshot below).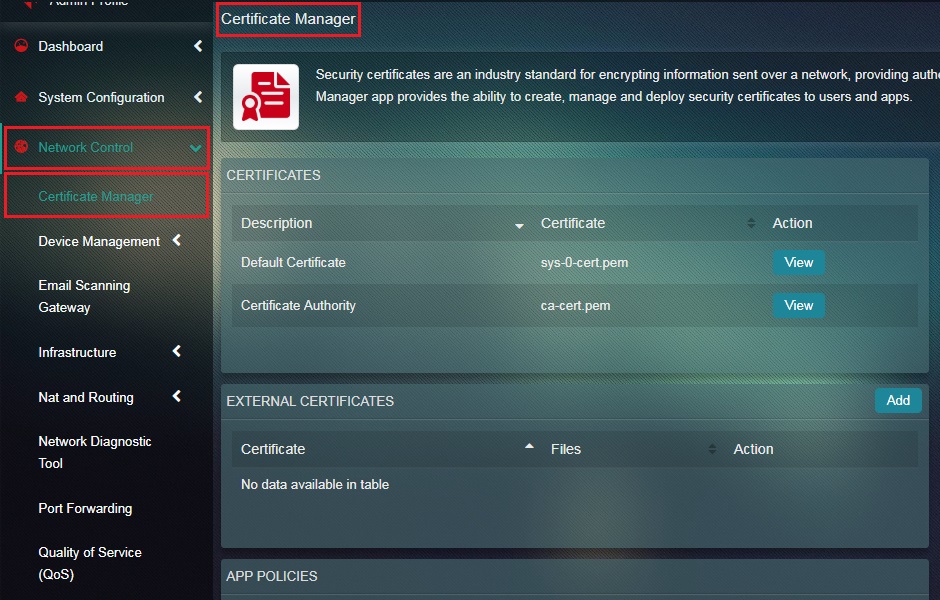
Step 5: Browse back to the SSL VPN application page. Click SSL VPN in the left-hand navigation menu under the SD-WAN category.
Step 6: You will now be directed to the SSL VPN application page. Click the Allow Connections button in the pink warning box and then click the Site to Site VPN tab.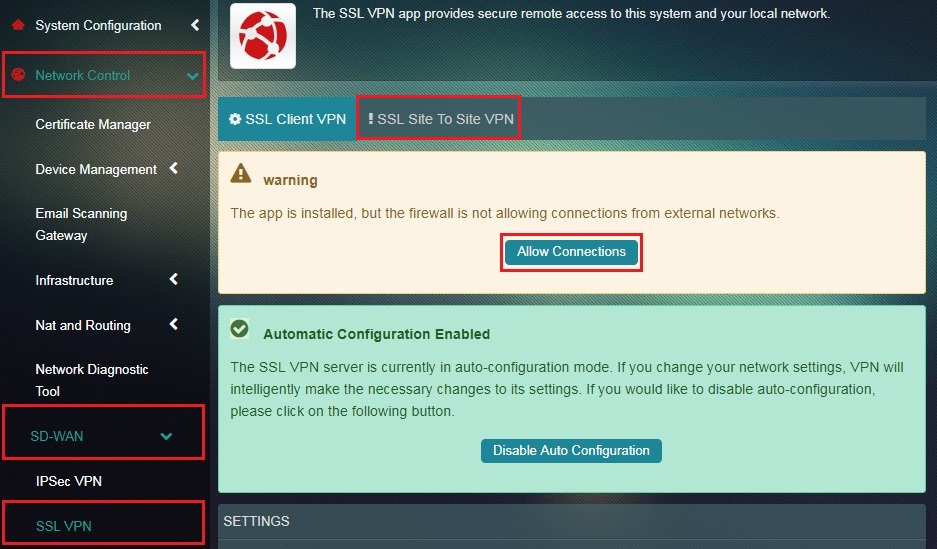
Step 7: Click the Configure button under the Configure this Crystal Eye Box as Headquarter section.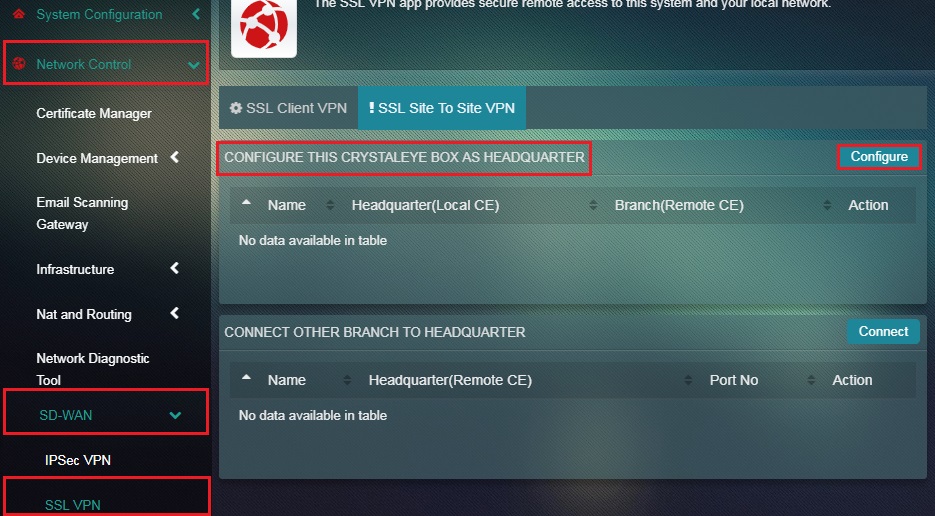
Note: This step must be performed in the Headquarter also known as the Local CE
You will now be directed to the Settings page. Crystal Eye auto populates certain networking related information related to the Headquarter (Local CE) and Branch (Remote CE).
In the Headquarter (Local CE) section, CE auto populates LAN IP Address, LAN Netmask, and VPN Endpoint IP Address. However, all of them can be customized as per requirement.
In the Branch (Remote CE) section, CE auto populates LAN Netmask and VPN Endpoint IP Address. Please note that the CE assigns a default VPN Endpoint IP Address and LAN Netmask for Branch which can be changed as per requirements.
The Administrator can also customize the Port for VPN which is assigned as 1195 by default.
Step 8: In the Settings page, enter the desired Name of the connection in the textbox under the General Settings section.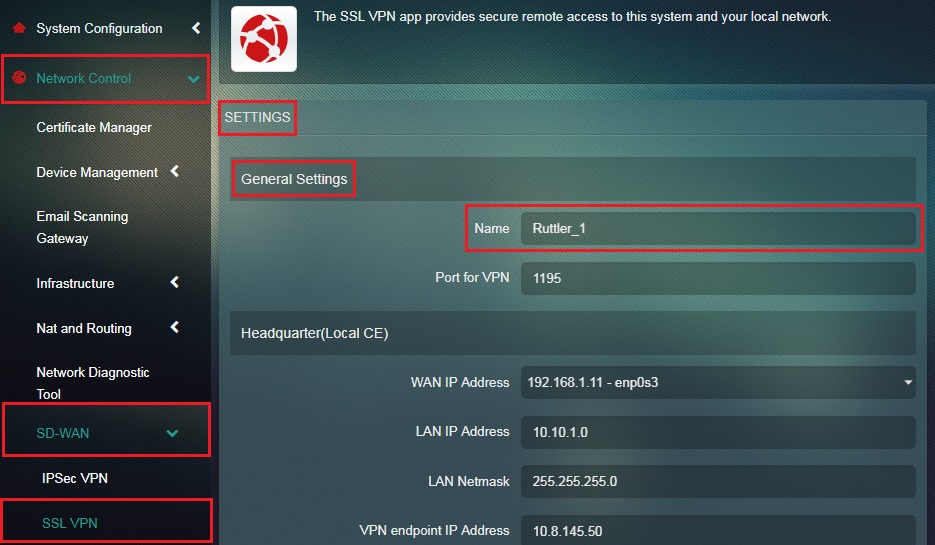
Note: This step must be performed in the Headquarter also known as the Local CE.
Step 9: Enter the Port for VPN in the textbox under the General Settings section.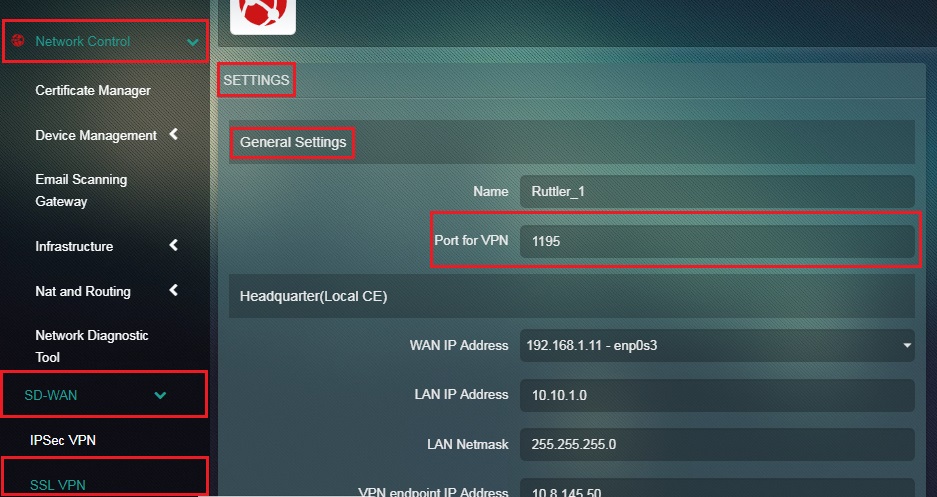
Note: The Administrator can also customize the Port for VPN which is assigned by default as 1195 by Crystal Eye. This step must be performed in the Headquarter also known as the Local CE
Step 10: Select the WAN IP Address of the Headquarter (Local CE) from the dropdown. 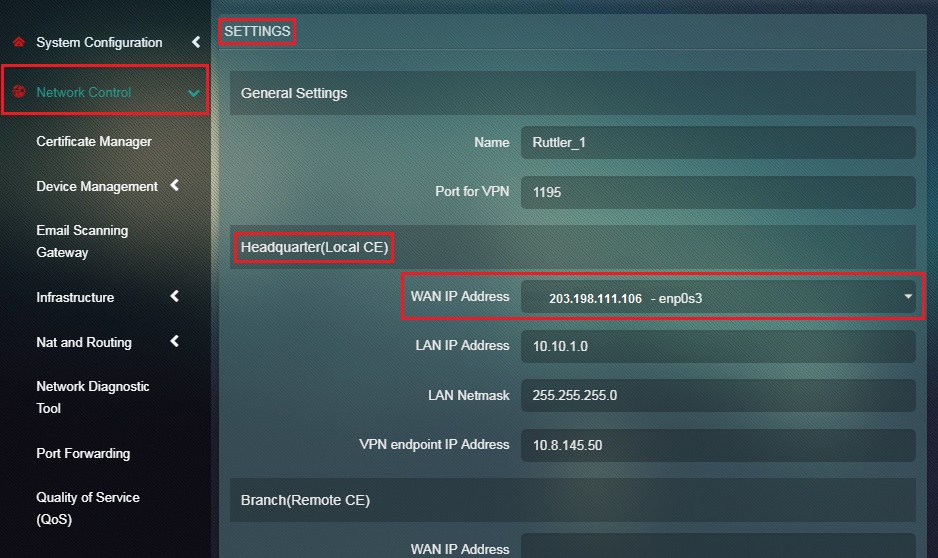
Note: Crystal Eye supports multi-wan connections henceforth in this scenario of multi-wan you will be able to see both the WAN IP Address in the dropdown. However, if the CE is connected to only one WAN connection the dropdown will display its local IP address. This step must be performed in the Headquarter also known as the Local CE.
Step 11: Enter the LAN IP Address of the Headquarter (Local CE) in the textbox.
Note: The LAN IP address is auto populated. However, you can also enter a customized IP address. 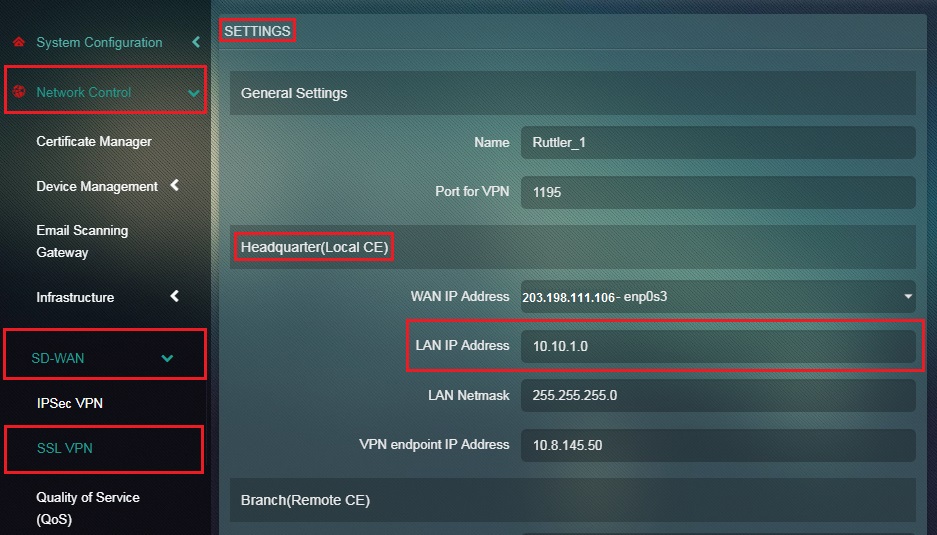
Step 12: Enter the LAN Netmask of the Headquarter (Local CE) in the textbox.
Note: The LAN Netmask of the Headquarter (Local CE) is auto populated.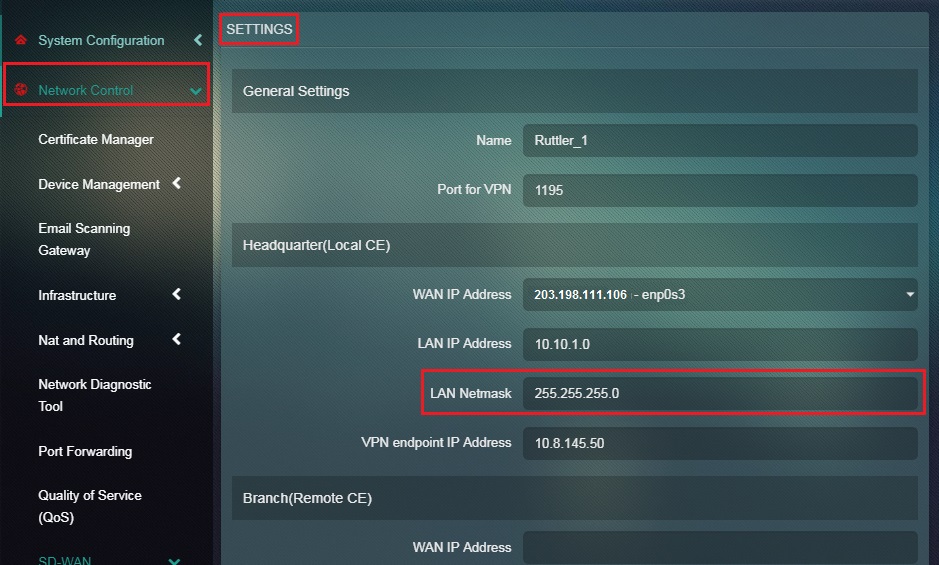
Step 13: Enter the VPN End Point IP Address of the Headquarter (Local CE) in the textbox.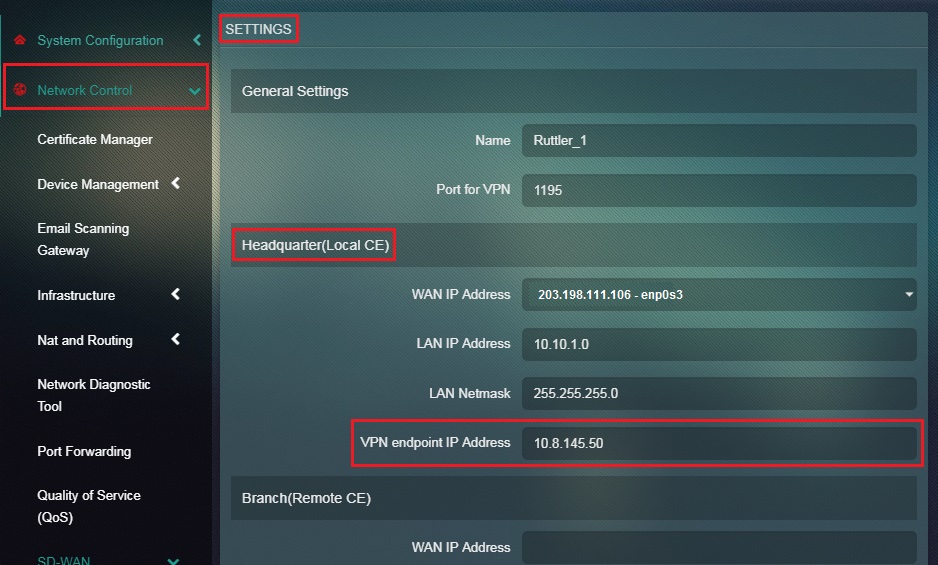
Note: The VPN End Point IP Address of the Headquarter (Local CE) is auto populated. However this IP address can be customized if required.
Step 14: Enter the WAN IP Address of the Branch (Remote CE) in the textbox.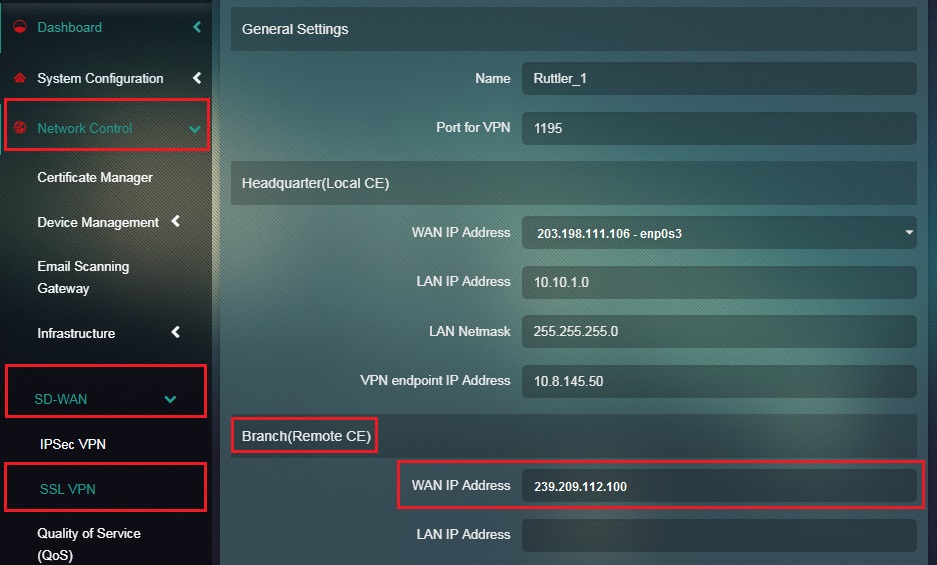
Note: This step must be performed in the Headquarter also known as the Local CE.
Step 15: Enter the LAN IP Address of the Branch (Remote CE) in the textbox.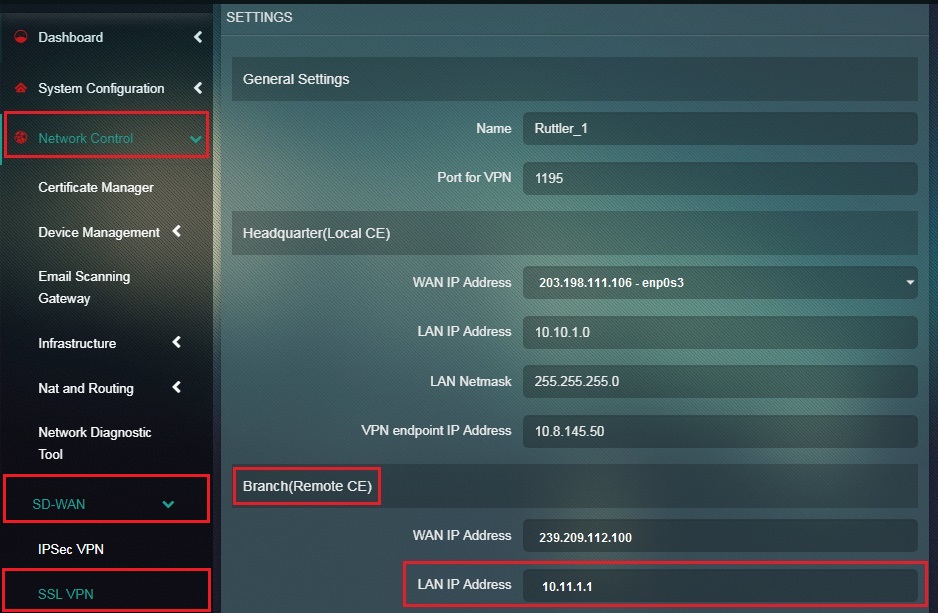
Note: This step must be performed in the Headquarter also known as the Local CE.
Step 16: Enter the LAN Netmask of the Branch (Remote CE) in the textbox.
Note: The LAN Netmask of the Branch (Remote CE) is auto populated.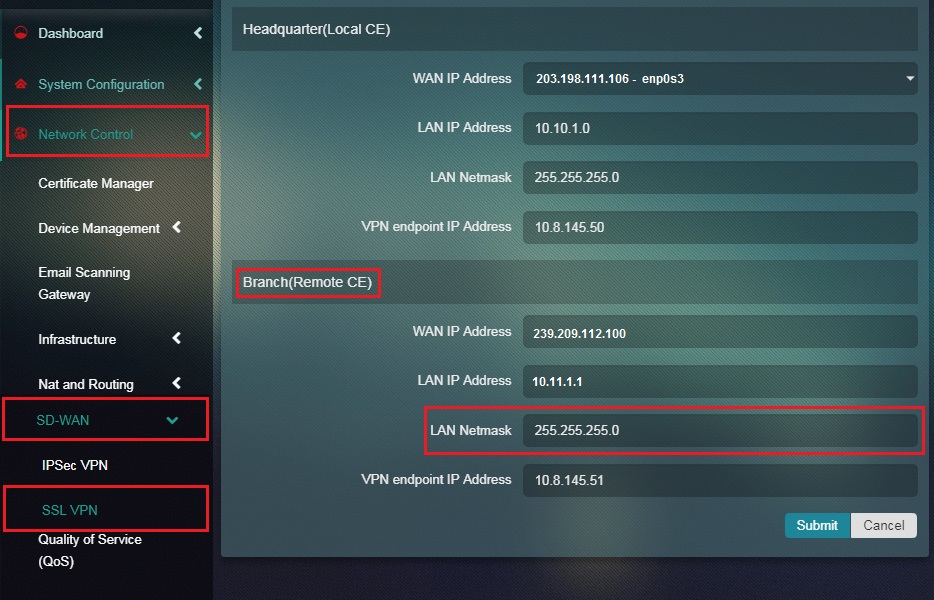
Step 17: Enter the VPN End Point IP Address of the Branch (Remote CE) in the textbox and click the Submit button.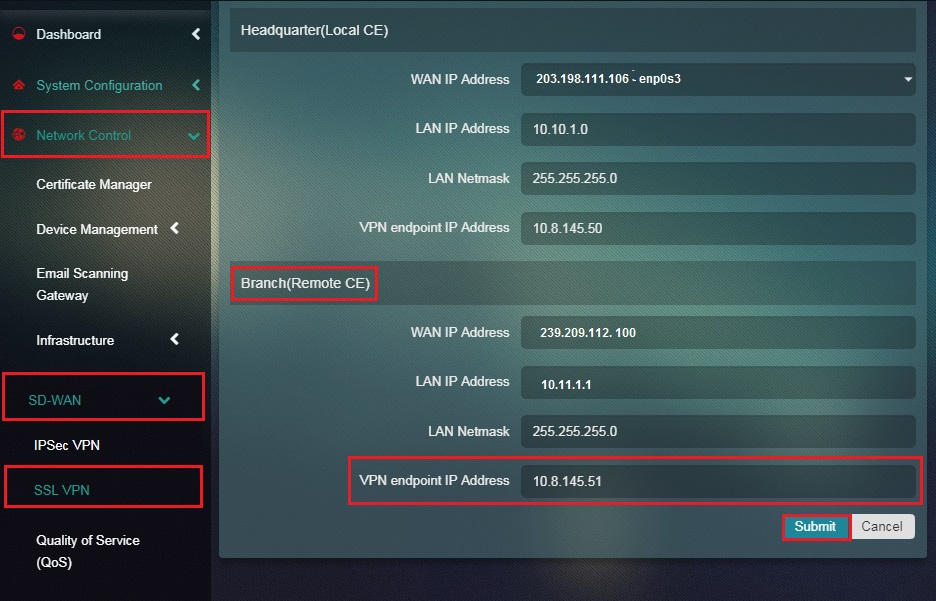
Note: The VPN End Point IP Address is auto populated. Once the Submit button is clicked, the user will be directed to the SSL VPN Site to Site page. The configured details of the Headquarter or Local CE would now be visible under the section “Configure This Crystal Eye Box as Headquarter” (refer to the screenshot below). 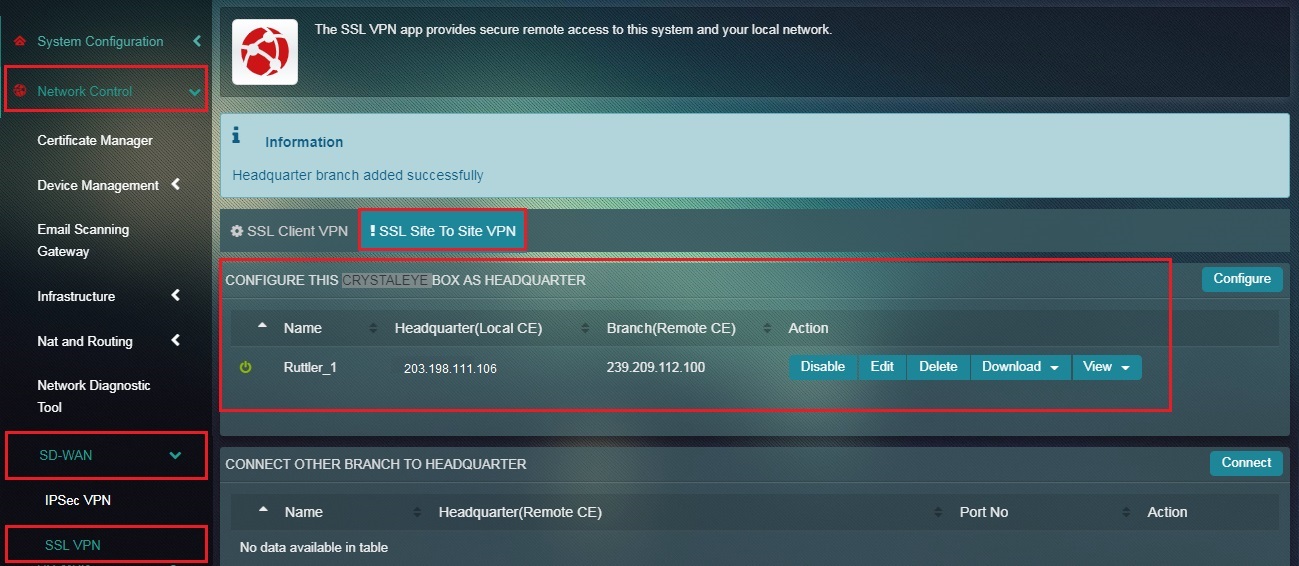
Phase II Configuration - The second phase deals with downloading the Key and Configuration File from the Headquarter and uploading it to the branch.
Step 18: You will now be directed to the SSL VPN app page. Click the Download dropdown and select Key for Branch and Configuration File for Branch. 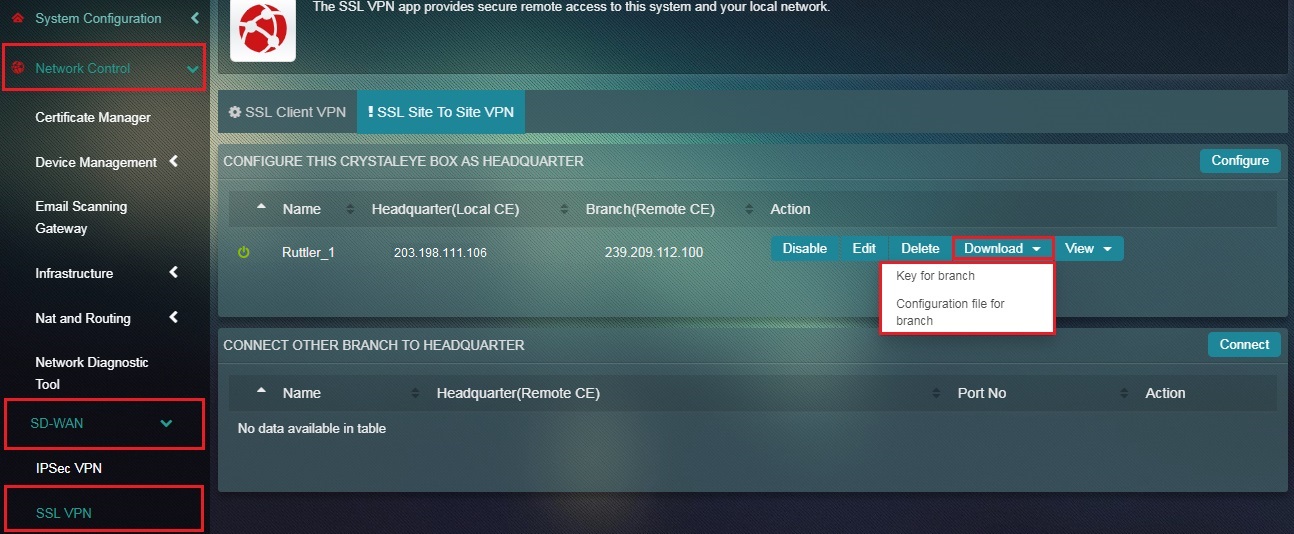
Note: This step must be performed in the Headquarter also known as the Local CE
Step 19: Click the Connect button under the Connect Other Branch to Headquarter section.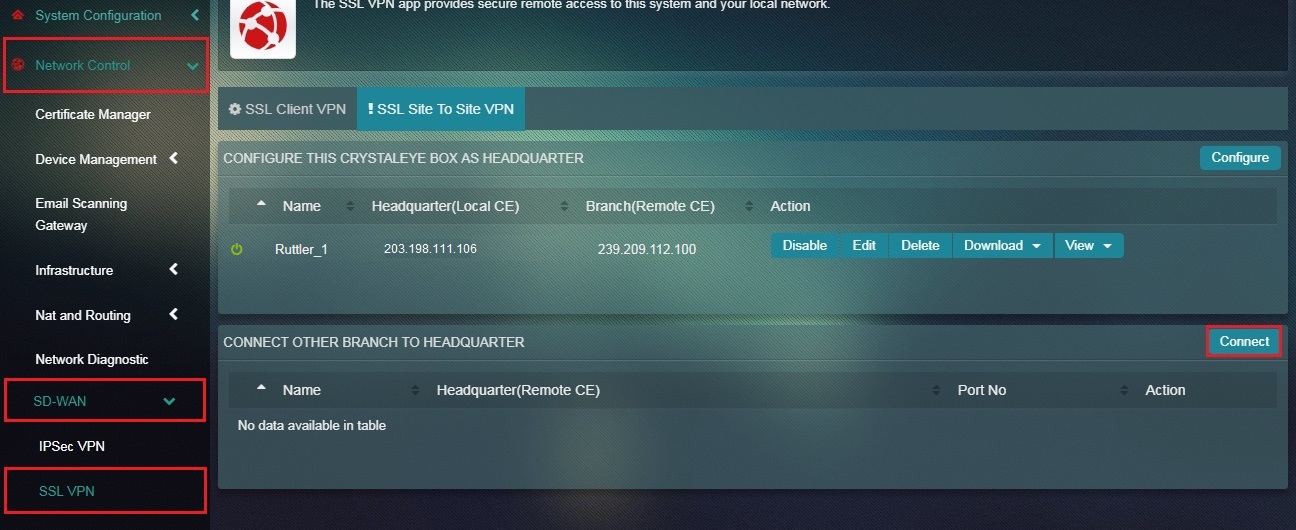
Note: This step must be performed in the Branch also known as the Remote CE.
Step 20: You will now see the Configure Branch page. Upload the Key and the Configuration File for Branch here and click the Upload button. 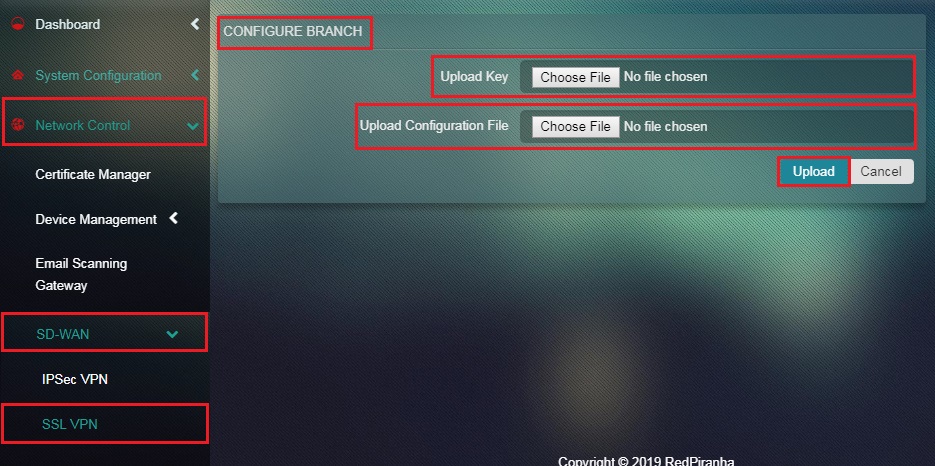
Note: This step must be performed in the Branch also known as the Remote CE. The Key and the Configuration File for Branch is the one downloaded from Headquarters or Local CE in step 18.