Incident and Event Services SIEM
The Incident and Event Services (SIEM) app helps to manage various settings that defines the levels of security analysis done by Red Piranha’s Security Operations Team. Crystal Eye offers three security service levels namely, Level – 1 Gold, Level 2 - Silver and Level 3 - Platinum. The system also prompts the user to feed in the primary and secondary contact details which is used to contact the users by Red Piranha Security Operations Team for various security related correspondences. The administrator can also start and stop the SIEM Agent installed in the Crystal Eye appliance.
Note: The SIEM Agent plays a vital role in connecting the CE XDR with Red Piranha’s SIEM Server and helps to pass the log files from the CE XDR to the server. These log files are then picked up by the CE SOC platform for further detailed security threat analysis by the Security Operations Team.
| Left-hand Navigation Panel > Compliance Control > Incident and Event Services (SIEM) Application |
|---|
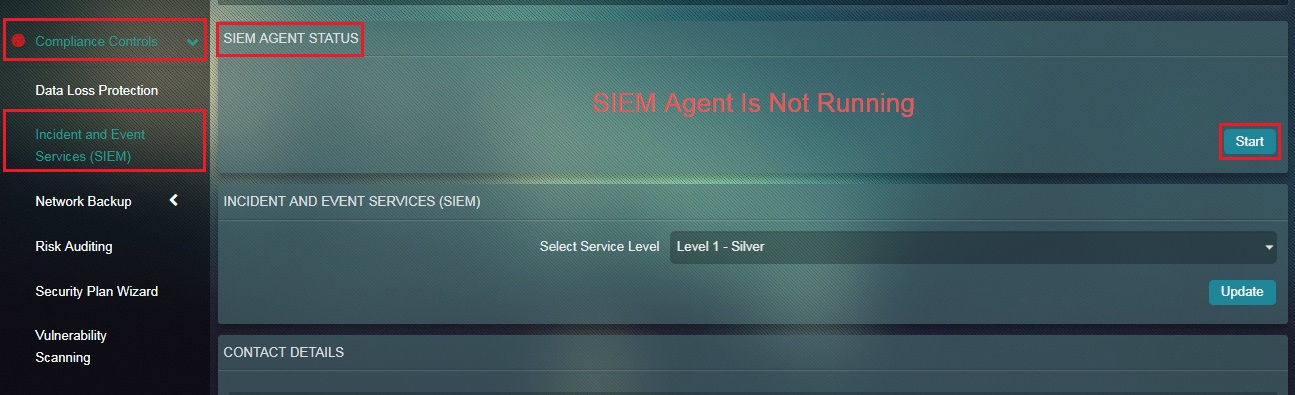
The SIEM Agent is a part of the Crystal Eye Platform and identifies various threats in the CE appliance through various types of log files and sends them to the SIEM Server for further analysis. The SIEM Agent Status section shows the current running status of the SIEM Agent and its operational status can be controlled through the Start and Stop button.
How to Start/Stop the Operational Status of the SIEM Agent?
Step 1: In the Incident and Event Services (SIEM) app page, click the Start/Stop button under the SIEM Agent Status section.
The Incident and Event Services (SIEM) app allows administrators to select the service levels of the SIEM. Based on these service levels selected by the user, various types of security related analytical services (as per service level agreement) are provided by Red Piranha’s Security Operations Team. Crystal Eye offers three service levels namely, Level – 1 Silver, Level 2 - Gold and Level 3 - Platinum. The SIEM agent (installed in the Crystal Eye appliance) analyses data from system log files and forwards it real time to the SIEM Server for further analysis and action. However, this process may vary according to the service levels opted which could either be Silver, Gold or Platinum.
How to Select the SIEM Service Levels?
Step 1: In the Incident and Event Services (SIEM) app page, select the Service Level from the dropdown and click the Update button.
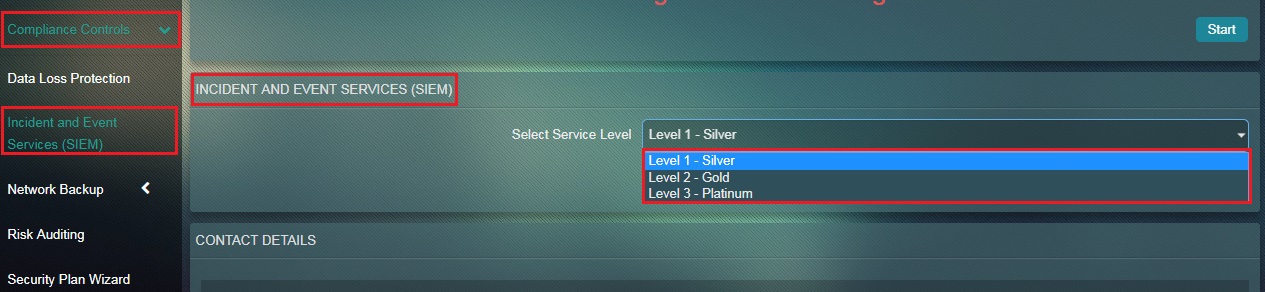
Note: The three service levels that the user can select are Level 1 – Silver, Level 2 – Gold and Level 3 – Platinum.
The system prompts the user to feed in the primary and secondary contact details which would be used by Red Piranha Security Operations Team for various security related correspondence with user.
Note: The user can select the preferred method of contact at the bottom of the section which can either be Phone, Mobile and Email.
How to Update Contact Details?
Step 1: In the Incident and Event Services (SIEM) app page, enter the Primary and Secondary Contact Details and click the Submit button under the Contact Details section.
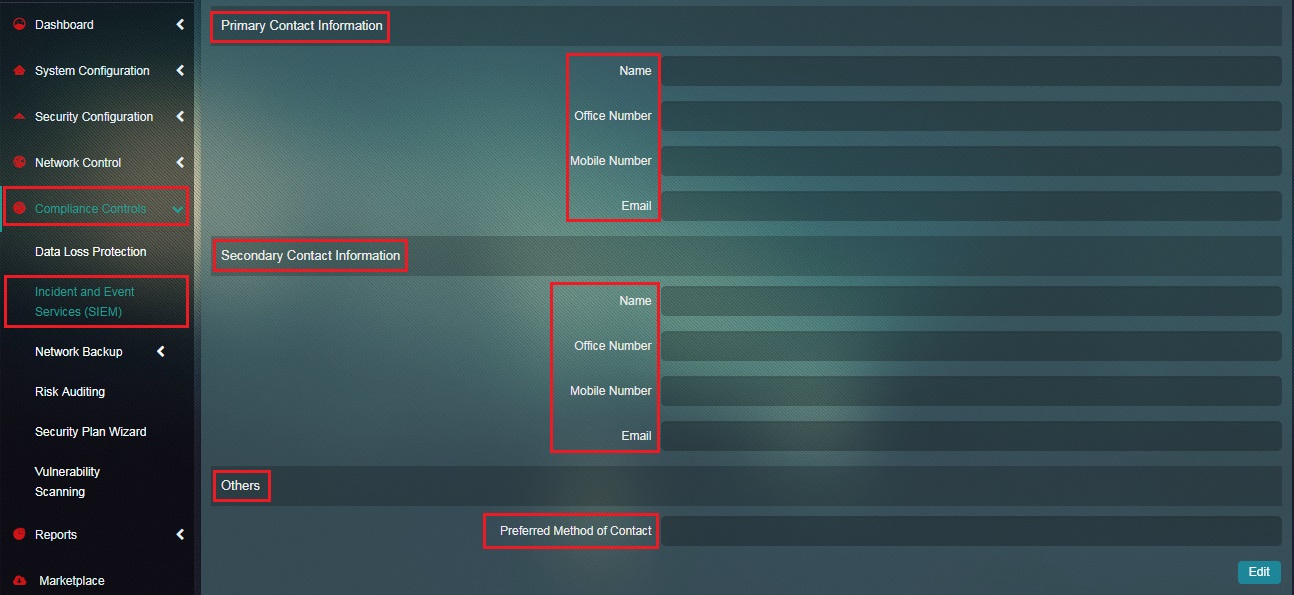
Note: The primary and secondary contact details would be used to contact the users by Red Piranha Security Operations Team for various security related correspondence. You may also specify the preferred method of contact which can be Phone, Mobile or Email.
There are various types of threat analysis done by the Security Operations Team of Red Piranha for its clients. These threat analytics sis are offered as a service as per the service level opted by the user under the Incident and Event Services (SIEM) section.
Red Piranha’s Security Operations Team delves into the log files generated from various default apps installed in the CE appliance which is sent by the SIEM agent to the SIEM Server. These log files give insights on the various threats patterns that can pose a risk to the network infrastructure.
The various threat analysis types performed by Red Piranha’s Security Operations Team based on the opted Service Levels are discussed in detail below.
- Integrity Check Logs Analysis: The system integrity directory is analysed
- Mail Logs Analysis: The log details of mail generated from mail app is analysed
- Message Logs Analysis: A list of system generated message logs are analysed for threats.
- Rootkit (Trojan) Analysis: Involves detection of any possible rootkit (Trojan) installed.
- Security Logs Analysis: The security logs generated from various applications of CE appliance is analysed for threats
- Web Configuration Logs Analysis: The CE appliance GUI related logs are analysed for threats.
- Anti-Virus Logs Analysis: It relates to analysis of the logs attained from the gateway anti-virus apps.
- Internet Browsing Analysis: This is done by analysing internet browsing related logs created through the content filter app
- Forcefield Logs Analysis: This analysis type is done to detect various forcefield app logs generated out of exceeding failed login attempts.
- Integrity Check Logs Analysis: The system integrity directory is analysed
- Mail Logs Analysis: The log details of mail generated from mail app is analysed
- Message Logs Analysis: A list of system generated message logs are analysed for threats.
- Rootkit (Trojan) Analysis: Involves detection of any possible rootkit (Trojan) installed.
- Security Logs Analysis: The security logs generated from various applications of CE appliance is analysed for threats
- Web Configuration Logs Analysis: The CE appliance GUI related logs are analysed for threats.
- Anti-Virus Logs Analysis: It relates to analysis of the logs attained from the gateway anti-virus apps.
- Internet Browsing Analysis: This is done by analysing internet browsing related logs created through the content filter app
- Data Loss Protection Logs Analysis: Operation logs generated from the DLP app is analysed to counter DLP incident.
- Database Log Analysis: Involves analysing various content database logs.
- Forcefield Logs Analysis: This analysis type is done to detect various forcefield app logs generated out of exceeding failed login attempts.